Protocols And Tools Used In Designing A Network Management
Network Management Protocols: A Guide to Understanding Them
Understanding network management protocols can be an arduous task.
It is easy to miss the technical term, the different procedures, the different ways of formatting the data, the multiple options, etc.
To facilitate this task we propose you to follow this simple guide.
Network management protocols are network protocols
The network administration protocols work in the field of networks and therefore are network protocols.
Now, it is important to differentiate them from those network protocols that allow the transfer of data between two devices, such as TCP, UDP, SMTP, CSMA / CD, etc.
In a network both data transfer protocols and administration protocols will coexist, sharing resources such as CPU and link bandwidth.
It is therefore interesting to keep in mind that network management protocols also influence the overall performance of the platform.
Be clear about the approach of the protocol
It is easy to understand that the more complex and heterogeneous the platform, the greater difficulty we will find in its administration.
Network administration has faced this complexity from three angles:
- Faults: in this area the idea is to have procedures to detect faults and a scheme to report them.
- Performance: here the idea is to obtain data on the behavior of the platform that allows us to make inferences about the performance of it.
- Actions: Many management protocols include the ability to execute actions on managed items.
When we try to understand a protocol it is important to stop for a moment and think about what angle the protocol proposes or with what angle we want to use it.
Network management protocols and their architecture
All management protocols propose an architecture and procedures to extract, collect, transfer, store and report management information from the managed elements.
It is important to understand the architecture and procedures when it comes to understanding a management protocol, and indispensable when implementing a solution based on this protocol.
Network management protocols and the organization of data
Another fundamental point is the way in which the network administration protocols format and manage the management data.
The basis is how they define and identify the elements to be administered. It is always interesting to mention: What element can I administer with this protocol? Only hardware or does it also cover applications, for example?
Then it is about defining what information I can extract from the managed elements and what actions I can execute, if I can execute any.
What format is used to handle the data? And how it is stored, if it is stored.
Finally, what are the options I have to access this information?
Now, in the rest of this article we will review three of the most popular administration protocols, trying to concentrate on the aforementioned points: focus, architecture and data organization.
For this review we will take the following diagram as a guide:
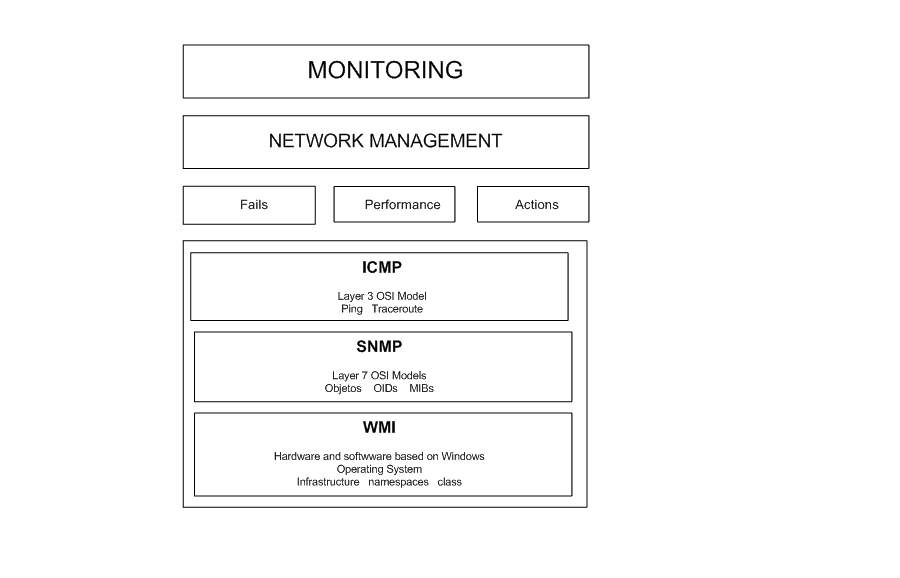
Diagram: The administration of networks and their protocols.
ICMP
ICMP (Internet Control Message Protocol) is a network layer protocol that is part of the group of sub-protocols associated with the IP protocol.
ICMP works in the field of fault validation and also allows the calculation of certain performance metrics.
The reader can read about the detailed specifications of the protocol in RFC792.
The procedure proposed by ICMP is based on the detection of an error condition and the sending of a message reporting said condition.
Thus, the key element is the messages contemplated by ICMP, which are usually classified in two categories:
- Error messages: Used to report an error in the packet transmission.
- Control messages: Used to report on the status of devices.
The architecture with which ICMP works is very flexible, since any device in the network can send, receive or process ICMP messages.
In practice it is used for routers and switches to report to the host that originates a packet that the packet can not be delivered due to a network error.
In addition, ICMP is also used to perform calculations of metrics on performance, such as levels of latency, response time or packet loss, among others.
SNMP
SNMP (Simple Network Management Protocol) is an application layer protocol that covers the areas of failures, performance and actions.
SNMP offers a scheme to gather, organize and communicate management information between the devices that make up a network.
This scheme manages to be common to a large number of hardware components, supporting:
- Diversity of devices: from network devices such as routers, switches, firewalls or access points to end user devices such as printers, scanners, stations or servers.
- Diversity of marks: most brands, when presenting a product, make sure that this product has support for SNMP included.
The reader interested in reading the formal SNMP specifications should review several RFC documents, but we recommend that you start with RFC 1157.
Architecture SNMP
The SNMP architecture is based on two basic components: the SNMP Agents and the SNMP Administrators. In the following diagram we present a basic outline of this SNMP architecture:
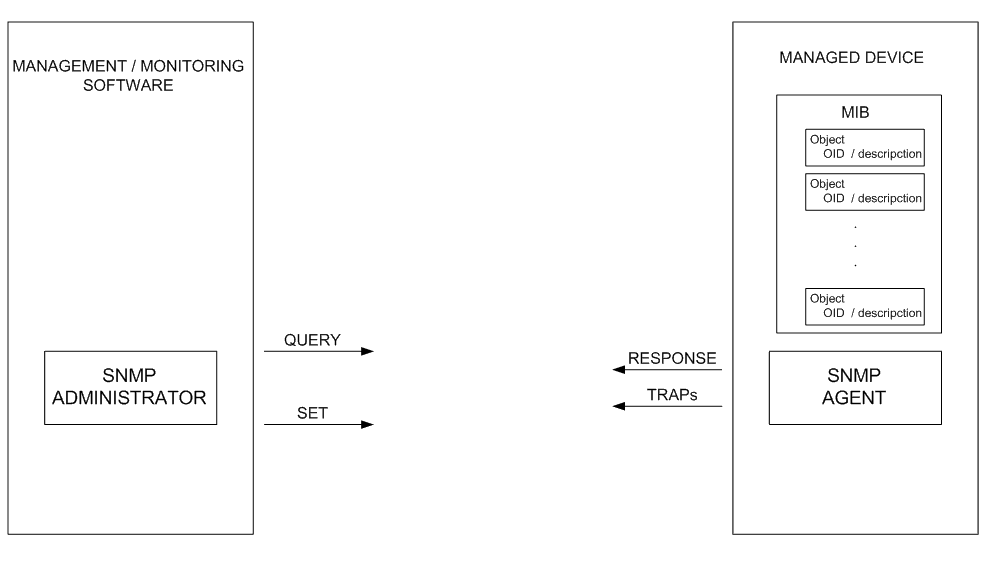
Description: SNMP Basic Architecture
SNMP agents are pieces of software that run on the elements to be managed. They are responsible for collecting data on the device. Then, when SNMP administrators request such data through queries, the agent will send the corresponding.
The SNMP agents can also send the SNMP Manager information that does not correspond to a query but that part of an event that occurs in the device and that requires to be notified. Then, it is said that the SNMP agent proactively sends a notification TRAP.
The SNMP Administrators are found as part of a management or monitoring tool and are designed to function as consoles where all the data captured and sent by the SNMP agents is centralized.
Organization of the data in SNMP
In SNMP the elements to be managed are called OBJECTS.
The OIDs (Object Identifier) are the elements that we use to uniquely identify objects. Surely you will have seen OIDs in a number format like:
.1.3.6.1.4.1.9.9.276.1.1.1.1.11
Actually these numbers are extracted from a system of hierarchical organization that starts by identifying the manufacturer of the device, to then identify the device and finally the object. In the following image we see an example of the scheme:
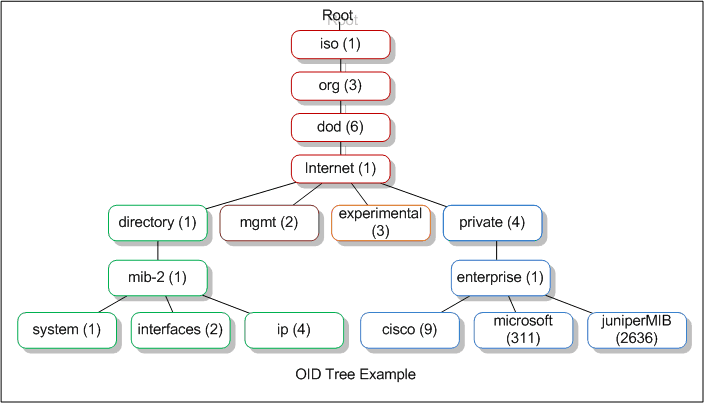
Description: NetFlow Architecture
Taken from: https://www.networkmanagementsoftware.com/snmp-tutorial-part-2-rounding-out-the-basics/
The MIBs (Management Information Base) are the formats that the data sent from the SNMP agents to the SNMP managers will comply with.
In practice, we have a general template with what we need to manage any device and then have individualized MIBs for each device, with their particular parameters and the values that these parameters can reach.
If you need to learn more about SNMP and monitoring based on this protocol, we invite you to review, in this blog, the article written by Carla Andrés on the subject.
WMI
With WMI (Windows Management Instrumentation) we will move in the universe composed by devices that run some Windows operating system and by the applications that depend on this operating system.
In fact, WMI proposes a model so that we can represent, obtain, store and share management information about Windows-based hardware and software, both locally and remotely.
On the other hand, in addition to what is associated with management information, WMI also allows the execution of certain actions.
WMI Architecture
The WMI architecture is composed of three fundamental entities. Let's look at the following diagram:
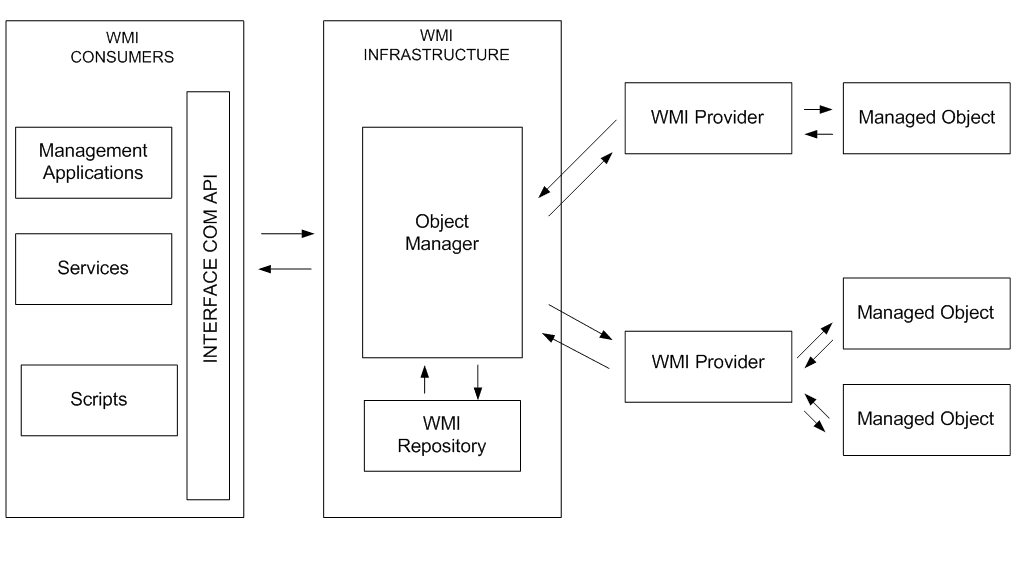
Description: Basic Architecture WMI
WMI Providers: A supplier is a piece in charge of obtaining management information from one or more objects.
The WMI infrastructure acts as an intermediary between suppliers and management tools. His responsibilities include the following:
- To obtain the data generated by suppliers in a planned way.
- To maintain a repository with all the data obtained in a planned way.
- To dynamically find the data requested by the administration tools, for which first a search will be made in the repository and, if the requested data is not found, a search will be made among the appropriate providers.
The administration applications correspond to the applications, services or scripts that use and process the information about the managed objects.
WMI manages to offer a uniform interface through which applications, services and scripts can be had requesting data and executing the actions proposed by the WMI providers on the objects to be administered.
Organization of the data in WMI
WMI is based on CIM (Common Information Model), which is a model that uses object-based techniques to describe different parts of a company.
This is a widely used model in Microsoft products; in fact, when Microsoft Office or an Exchange server is installed, for example, the extension of the model corresponding to the product is automatically installed.
Just that extension that comes with each product is what is known as WMI CLASS. A class describes the object to be managed and all that can be done with it.
This description starts from the attributes that the class handles, such as:
- Properties that refer to the objects' own characteristics, such as their name, for example.
- Methods that refer to the actions that can be carried out on the object, such as ¨holding¨ in the case of an object that is a service.
- Associations that refer to possible associations between objects.
Now, once WMI providers use object classes to collect management information and this information passes to the WMI infrastructure, it is required to organize it in some way.
This organization is achieved through logical containers called namespaces, which are defined by administration area and contain the data that comes from the related objects.
Namespaces are defined under a hierarchical scheme reminiscent of the scheme followed by folders on a disk. So, the namespace root is the top of this hierarchical scheme and root/CIMv2 is the default namespace.
One analogy that many authors use to explain the organization of data in WMI is to compare WMI with databases.
So, we know that the classes correspond to the tables, the namespaces to the databases and the WMI infrastructure to the database handler.
So this is the review of network administration protocols. To finish, we must indicate that all monitoring tools use at least one network administration protocol to meet their objectives.
Pandora FMS works with these three protocols to offer a wide and flexible general purpose monitoring tool.
If you still don't know the multiple advantages that Pandora FMS can offer to your organization and it has more than 100 devices to monitor, talk to the sales team of Pandora FMS to obtain a free trial of the most flexible monitoring software in the market: https://pandorafms.com/free-demo/
Also, remember that if your monitoring needs are more limited you have at your disposal the OpenSource version of Pandora FMS. Find more information here: https://pandorafms.org/
Don't hesitate to send your questions. Our Pandora FMS team will be delighted to help you!
![]()
El equipo de redacción de Pandora FMS está formado por un conjunto de escritores y profesionales de las TI con una cosa en común: su pasión por la monitorización de sistemas informáticos.
Pandora FMS's editorial team is made up of a group of writers and IT professionals with one thing in common: their passion for computer system monitoring.
Protocols And Tools Used In Designing A Network Management
Source: https://pandorafms.com/blog/network-management-protocols/
Posted by: mccluskeyvarty2001.blogspot.com

0 Response to "Protocols And Tools Used In Designing A Network Management"
Post a Comment