Incomplete Coverage Of A Topic Violates Which Of These Four Writing Criteria?
Earlier chapters introduced the Institute of Medicine (IOM) committee's conceptualization of health database organizations (HDOs), outlined their presumed benefits, listed potential users and uses, and examined issues related to the disclosure of descriptive and evaluative data on health care providers (institutions, agencies, practitioners, and similar entities). This chapter examines issues related to information about individuals or patients—specifically, what this committee refers to as person-identified or person-identifiable data. It defines privacy, confidentiality, and security in the context of health-related information and outlines the concerns that health experts, legal authorities, information technology specialists, and society at large have about erosions in the protections accorded such information. It pays particular attention to the status that might be accorded such data when held by HDOs.
Existing ethical, legal, and other approaches to protecting confidentiality and privacy of personal health data offer some safeguards, but major gaps and limitations remain. The recommendations at the end of this chapter are intended to strengthen current protections for confidentiality and privacy of health-related data, particularly for information acquired by HDOs.
HISTORICAL PERSPECTIVES AND GENERAL OBSERVATIONS ON DISCLOSURE OF INFORMATION
The Privacy Protection Study Commission (PPSC) was created by the Privacy Act of 1974 to investigate the personal data recordkeeping practices of governmental, regional, and private organizations. In its landmark 1977 report, Personal Privacy in an Information Society (PPSC, 1977a), the commissioners noted that:
Every member of a modern society acts out the major events and transitions of his life with organizations as attentive partners. Each of his countless transactions with them leaves its mark in the records they maintain about him.
The report went on to point out that:
... as records continue to supplant face-to-face encounters in our society, there has been no compensating tendency to give the individual the kind of control over the collection, use, and disclosure of information about him that his face-to-face encounters normally entail.
The warnings implicit in the commissioners' statement are even more pertinent today. The emergence of HDOs in the 1990s comes at a time when the American public is expressing growing concern about threats to personal privacy. A 1993 Louis Harris poll found that 79 percent of the American public is "very" (49 percent) or "somewhat" (30 percent) worried about the threat to personal privacy (Harris/Equifax, 1993).1 This response has remained stable since 1990 when it rose sharply from a figure of 64 percent cited for 1978. There was agreement by 80 percent of respondents that "consumers have lost all control over how personal information about them is circulated and used by companies." The 1992 survey also asked about the effect of computers on privacy. Sixty-eight percent agreed strongly or very strongly that "computers are an actual threat to personal privacy," and almost 90 percent agreed that computers have made it much easier to obtain confidential personal information improperly (Equifax, 1992).
Many privacy experts have described the ready availability of personal information (e.g., see Piller, 1993). Rothfeder (1992) asserts that about five billion records in the United States describe each resident's whereabouts and other personal information. He also claims that such information is moved from one computer to another about five times a day (pp. 22-23):
Information about every move we make—buying a car or a home, applying for a loan, taking out insurance, purchasing potato chips, requesting a government grant, getting turned down for credit, going to work, seeing a doctor—is fed into ... databases owned by the credit bureaus, the government, banks, insurance companies, direct marketing companies, and other interested corporations. And from these databases it's broadcast to thousands ... of regional databanks as well as to numerous information resellers across the country.
Rothfeder believes that such pervasive data acquisition and exchange can lead to a feeling of powerlessness in the face of privacy intrusion. His language is evocative (p. 30):
Increasingly, people are at the whim of not only pressure groups, but also large organizations—direct marketers, the credit bureaus, the government, and the entire information economy—that view individuals as nothing but lifeless data floating like microscopic entities in vast electronic chambers, data that exists [sic] to be captured, examined, collated, and sold, regardless of the individual's desire to choose what should be concealed and what should be made public.
It may be that the increasing aggregation of personal data documenting the details of our physical attributes and defects, behaviors, desires, attitudes, failings, and achievements creates a virtual representation of us. Some have called this a ''computerized alter ego" or a "digital version of each of us to go with our public personae" (Rothfeder, 1992, p. 16, citing Miller). To the extent this is so, the privacy of this "virtual person" requires protection.
Recently the U.S. Congress has given serious attention to reform of the Fair Credit Reporting Act (Public Law [P.L.] 102-550; see below). It has also looked at technology-driven privacy issues: most pertinent are legislative proposals to restrict caller I.D. programs (S. 652; H.R. 1305; also see, House Report No. 102-324, 102nd Congress 2d Session), junk telephone calls and junk faxes (P.L. 102-243, "Telephone Consumer Protection Act of 1991"). Some congressional efforts, such as bills related to DNA testing and genetic profiling (S. 1355, "DNA Identification Act of 1991"; H.R. 2045, "Human Genome Privacy Act"), were intended to protect individuals against threats posed by medical technologies or initiatives. In October 1991, the Committee on Government Operations of the U.S. House of Representatives, Subcommittee on Government Information, Justice, and Agriculture, held hearings on genetic privacy issues, and in April 1992 it issued a report calling for reforms related to the privacy of genetic information.
Both the U.S. Congress and the Administration have undertaken activities related to the protection of medical information. In October 1993 the Senate Committee on the Judiciary held hearings on High Tech Privacy Issues in Health Law, and in November, the Subcommittee on Government Information, Justice, and Agriculture of the Committee on Government Operations held a hearing on a report prepared by the Office of Technology Assessment (OTA, 1993) at the request of that subcommittee and the Senate Subcommittee on Federal Services, Post Office, and Civil Service. The former committee has also been drafting legislation to protect the privacy of health information.2
A Task Force on Privacy was established in 1990 by the Assistant Secretary for Planning and Evaluation to report on the privacy of private sector health records. Another DHHS group established at the same time, the Workgroup on Electronic Data Interchange (WEDI, 1991) also addressed the protection of information when medical insurance claims are handled electronically. The recommendations of that workshop are discussed later in this chapter.
Two of President Clinton's Health Care Reform Task Forces met during the spring of 1993. They considered the implications of and generated plans for the protection of health-related data that would be acquired and held under the administration's proposal for health reform. The legislative proposals in the Health Security Act contain specific privacy protection provisions.3
forms governing disclosure of such information; and (3) the development of technology to implement standards regarding such information. It should also establish education and awareness programs, foster adequate security practices, train personnel of public and private entities in appropriate practices.
Sec. 5122. calls for a proposal not later than three years after enactment of the HSA to provide a comprehensive scheme of Federal privacy protection for individually identifiable health information that would include a Code of Fair Information Practices and provide for enforcement of the rights and duties created by the legislation. (Health Security Act. Title V. Part 2. Privacy of information.)
State legislatures have also been active. In the past three years, for example, many states have adopted legislation that prohibits employers from discriminating against applicants and employees on the basis of off-the-job, lawful activity or some specific subset of lawful activity, such as cigarette smoking.
SOURCES OF CONCERNS ABOUT PRIVACY AND THE CONFIDENTIALITY OF HEALTH RECORDS
Two somewhat distinct trends have led to increased access to the primary health record and subsequent concerns about privacy. One has to do with primary health records regardless of how they are created and maintained; the other involves health records stored electronically.
Health Care Records
The quantity and type of health care information now collected has also increased dramatically in recent years. The participation in health care delivery of many different individuals and groups of providers exerts strong pressures to document in ever greater detail. The expanding numbers of available technologies for diagnosis and therapy mean that details that a provider could at one time recall must now be recorded and thus become available for inspection by others. Further, information on lifestyle (e.g., use of tobacco or alcohol), family history, and health status have become of greater interest and relevance as we learn more about the relationship of these factors to overall health and well-being. In addition, genetic data are becoming more readily available, not only for prenatal testing but also for assessing an individual's degree of risk for an inherited condition.4
The more detailed the information about an individual or class of individuals, the more appropriate, one hopes, is the treatment they will be given. Further, documentation of care and risk factors are essential to promoting continuity of care over time and among providers. It is also a first defense against charges of malpractice.
The primary health record is no longer simply a tool for health care providers to record their impressions, observations, and instructions. Rather, it serves many purposes beyond direct health care. Third-party payers access patient record information to make payment determinations, and managed care organizations access patient records for precertification and case management.
Other parties external to the healing relationship seek person-identified information and assert socially beneficial reasons for access. What was once the "business" only of patients and possibly their physicians has now become the business of such groups as: (1) officers of government entitlement programs checking on eligibility, and on patient and provider fraud and abuse; (2) agencies granting security clearance; (3) attorneys bringing criminal or civil charges; and (4) social service workers protecting possibly abused children, to name only a few. Others access secondary health records or obtain portions of the medical record when making decisions about hiring, granting a license, or issuing life, health, or disability insurance.
Electronic Records
Other trends give rise to particular concerns about the confidentiality of health information that is stored electronically. First is the ability to access, transmit, and copy large volumes of data easily. Photocopying paper records is, of course, possible, but it is hardly feasible for large numbers of geographically dispersed medical records. Electronic storage and transmittal of data, by contrast, enable interested parties to aggregate information for individuals over time and across institutions and providers of care.
Second, databases were at one time discrete—often held in physically secure rooms on tape drives—with identifiers that were unique to a given institution or insurer. Now, however, data from diverse sources can be combined and linked. Once data are stored electronically, networks of databases can be explored almost imperceptibly from remote locations. Unless security systems are designed to record access, the curious, entrepreneurial, or venal can enter databases without leaving evidence of having done so.
Third, computer-based health data have become a very valuable commodity. Some companies obtain information from physicians' computers and pharmacy records for sale to pharmaceutical companies in return for incentives such as low-cost computer hardware and software. These companies gather such identifying variables as age, sex, and Social Security numbers even if patient names are either not taken or are later stripped off (Miller, 1992).
Other companies resell information from prescription or claims databases to companies that sort it by physician for marketing purposes. For example, Health Information Technologies, Inc., helps automate private physicians' insurance claims. When it transmits claims and payments between the insurance company and the physician, it retains electronic copies of these records, and it can later sell them (presumably without physician or patient names) for pharmaceutical and other related kinds of marketing (Miller, 1992).
In August 1993, Merck & Company purchased Medco Containment Services, a mail-order prescription firm. The purchase price, $6 billion, was based in part on the value of the information in its databases to influence physician prescribing practices (Tanouye, 1993). HDOs will control a gold mine of information, and they may find it difficult indeed to resist economic benefits from allowing access to their data files by third parties.
Finally, because developers of HDOs have compared claims transmittal to electronic funds transfer (EFT), it is helpful to examine how the Privacy Protection Study Commission regarded confidentiality in EFT. The commissioners were alert to problems that might result if records created by EFT could not be controlled by institutions. Noting that automated clearinghouses centralize information that would otherwise be segregated among diverse depository institutions, their report (PPSC, 1977a) expressed worry about threats posed by the accumulation and centralization of the financial information that flows through such clearinghouses. The commissioners also recognized that the resulting pools of information would become attractive sources of person-identifiable information for use "in ways inimical to personal privacy" (p. 121). They urged that adequate protections be established for person-identifiable information flowing through an EFT data communications network and that such account information be retained for as limited a period of time as was essential to fulfill operating requirements of the service provider. Thus, in contemplating EFT, the commissioners did not foresee, and certainly did not encourage, the creation of an information repository now contemplated under the concept of an HDO.
DEFINITIONS
Below, the committee offers definitions of critical terms—privacy (especially informational privacy), confidentiality, security, and health-related information.
Privacy
The most general and common view of privacy conveys notions of withdrawal, seclusion, secrecy, or of being kept away from public view, but with no pejorative overtones. By contrast, an invasion of privacy occurs when there is intentional deprivation of the desired privacy to which one is entitled. In public policy generally and health policy in particular, privacy takes on special meanings, some derived from moral theories, others from legal doctrine, and one from the widespread use of health information.
Privacy is sometimes characterized as the "right to be left alone" (Cooley, 1880; Warren and Brandeis, 1890; Elison and Nettiksimmons, 1987; Turkington, 1987; Herdrich, 1989). Many experts, however, have objected that such a definition is too broad to be helpful in the health context. There are innumerable ways of not being left alone that arguably have nothing to do with privacy (Thomson, 1975; Reiman, 1976; Parent, 1983), such as when an individual is subjected to aggressive panhandling on a city street. Consequently, theorists have sought to refine their conceptions of privacy. Their aim has been to isolate what is unique about privacy, to identify what constitutes its loss, and to distinguish among a variety of conceptually related but separable senses of privacy (Gerety, 1977; McCloskey, 1980; Schoeman, 1984).
The development and application of the concept of privacy in American law encompasses three clusters of ideas.5 First, privacy embodies autonomy interests; it protects decisions about the exercise of fundamental constitutional liberties with respect to private behavior, such as decisions relating to marriage, procreation, contraception, family relationships, and child-rearing. This is frequently characterized as decisional privacy (Tribe, 1978). Second, privacy protects against surveillance or intrusion when an individual has a "reasonable expectation of privacy." Examples include protections against unlawful searches of one's home or person and unauthorized wiretapping. Third, privacy encompasses informational interests; this notion is most frequently expressed as the interest of an individual in controlling the dissemination and use of information that relates to himself or herself (Shils, 1966; Westin, 1967), or to have information about oneself be inaccessible to others. This last form-informational privacy-is the main subject of this chapter.
Informational Privacy
Informational privacy—"a state or condition of controlled access to personal information" (Schoeman, 1984; Allen, 1987; Powers, 1993)—is infringed, by definition, whenever another party has access to one's personal information by reading, listening, or using any of the other senses. Such loss of privacy may be entirely acceptable and intended by the indi vidual, or it may be inadvertent, unacceptable, and even unknown to the individual.
This definition of privacy thus reflects two underlying notions. First, privacy in general and informational privacy in particular are always matters of degree. Rarely is anyone in a condition of complete physical or informational inaccessibility to others, nor would they wish to remain so. Second, although information privacy may be valuable and deserving of protection, many thoughtful privacy advocates argue that it does not, in itself, have moral significance or inherent value (Allen, 1987; Faden, 1993).
Nonetheless, informational privacy has value for all in our society, and it accordingly has special claims on our attention. In his pivotal book, Privacy and Freedom, Westin (1967) described it as "the claim of individuals, groups, or institutions to determine for themselves when, how, and to what extent information about them is communicated to others" (p. 7). This definition served as the foundation for the Privacy Act of 1974 (P.L. 93579; 5 U.S.C. § 552a). This act, arguably the most significant step to protect privacy in recent decades, was enacted to control use of personally identifiable information maintained in federal government databases.
Recordkeeping Privacy
In recent decades, discussions about privacy have almost exclusively addressed the use of information about people to make decisions about some right, privilege, benefit, or entitlement—so-called "recordkeeping privacy." This focus was of particular interest to those framing the Privacy Act of 1974.
More recently the desire for informational privacy has become an important expectation, not because of a benefit or entitlement sought, but for its own sake. Information may be created as a byproduct of some event—for example, an individual's geographic location becomes available when he or she uses a bank card for a financial transaction; similarly, one's preferences are known when one buys goods by mail order or uses a check-verification card at the local supermarket. In yet other cases, information derives from aggregating data from many sources, including public records; such aggregation can also include data that have been derived from computer processing (e.g., buying profiles or dossiers).
Data subjects want informational privacy to be respected in such contexts as well. Many people in the United States would like to believe that data collected about them legitimately, in connection with some transaction or incidentally through participation in the general activities of society, will not be exploited for secondary purposes such as advertising, soliciting, telemarketing, promotional activities, or other actions that are distinct from and unrelated to the activities for which the data were originally collected (see Harris/Equifax, 1993). As should be clear from the discussion in this chapter, however, these hopes are often not realized in general or in relation to health information.
Privacy Rights
To assert a right is to make a special kind of claim. Rights designate some interests of the individual that are sufficiently important to hold others under a duty to promote and protect, sometimes even at the expense of maximizing or even achieving the social good (Raz, 1986). Two interests are widely cited as providing the moral justification for privacy rights: the individual's interest in autonomy and the instrumental value that privacy may have in promoting other valuable human goods.
With respect to autonomy, privacy fosters and enhances a sense of self (Reiman, 1976). Respecting privacy enhances an individual's autonomy (Westin, 1967; Benn, 1971; Bloustein, 1984). It allows the individual to develop the capacity to be self-governing or "sovereign," a notion analogous to the sense in which autonomous states are sovereign (Beauchamp and Childress, 1989). The loss or degradation of privacy can enable others to exercise an inordinate measure of power over the individual's economic, social, and psychological well-being (Gavison, 1980; Parent, 1983).
With respect to the value of privacy to promote other ends, its instrumental value, privacy permits the development of character traits and virtues essential to desirable human relationships. These include trust, intimacy, and love. Without some measure of privacy, these relationships are diminished or may not be possible (Fried, 1968; Rachels, 1975).
The existence of informational privacy rights means that someone is under a duty either not to disclose information or to prevent unauthorized access to information by others. Dworkin (1977) has argued that for a right to be meaningful implies that any policy or law overriding such duties must withstand rigorous scrutiny and that considerations of social utility alone are inadequate grounds to override it. That is, to take rights seriously is to recognize some limits on the prerogative of government or others to mandate the common good at the expense of the individual. This is not to say, however, that rights function as an absolute barrier to the pursuit of collective goals; indeed, the tension between individual and social goals is reflected in the issues raised in Chapter 3, as well as in this chapter.
Balancing Benefits of HDOs Against Loss of Informational Privacy
There cannot be much doubt that HDOs will serve legitimate societal interests as described in Chapter 2. Nevertheless, because HDOs will represent one of the most comprehensive and sensitive automated personal record databases ever established, they inevitably implicate interests protected by informational privacy principles. Accordingly, HDO advocates will be well served from an ethical as well as legal viewpoint if they consider what social goods justify possible loss of privacy and such loss can be minimized or prevented.
Whether HDOs can achieve their potential for good in the face of their possible impact on privacy will likely turn on the interplay of three considerations. First, to what extent do the HDOs provide important (and perhaps irreplaceable) health care benefits to their regions and perhaps to the nation? Second, do the societal benefits resulting from the implementation of HDOs outweigh the privacy risks? Third, to what extent have adequate privacy safeguards been incorporated into the HDOs?
Federal and State Privacy Protection
No explicit right to privacy is guaranteed by the Constitution of the United States; in fact, the word "privacy" does not appear. The presumed right as the basis of a civil action is based on legal opinion written by Justice Louis D. Brandeis in 1890, and its constitutional status derives from various amendments to the Bill of Rights.
The issues surrounding the constitutional status of privacy protection are too numerous and controversial to explore in detail here. Most constitutional scholars agree that federal constitutional protections are unlikely to provide the first line of defense for privacy of health information. The Constitution generally has not provided strong protection for the confidentiality of individual health care information; the constitutional protection for informational privacy is thus very limited and derived from case law interpreting the Constitution.
The courts have made clear that, at least theoretically, information privacy principles based on the Constitution limit a government agency's collection and use of personal information to situations in which the use bears a rational relationship to a legitimate governmental purpose. The government's interest in the information program must outweigh the threat to personal privacy posed by the program.6
In Whalen v. Roe (429 U.S. 589 [1977]), for example, the Supreme Court balanced the privacy threat posed by a New York State law against the statute's benefits. The New York State statute required pharmacists and physicians to report sensitive health record information to state officials, in this case prescriptions for controlled drugs. It required physicians to report the names of patients receiving certain types of prescription drugs to a state agency. The court concluded that the statute was constitutional on two grounds: the societal interests served by the statute (combating the illegal use of otherwise legal drugs) and extensive privacy and confidentiality protections in the law (redisclosure of the drug information, for example, was prohibited). The court suggested that if the statute had lacked these confidentiality protections it would have been found to violate constitutional privacy principles (Chlapowski, 1991). Thus, privacy rights are to be considered derived and not explicit rights.
In United States v. Westinghouse Electric Corp. (638 F. 2d 570, 578 [3rd Cir. 1980]), the Third Circuit identified seven factors that should be weighed in determining whether to permit a government agency to collect personal information and thus undertake a program that infringes privacy. These were the type of record requested; the subject matter of the information; the potential for harm in a subsequent nonconsensual disclosure; the damage to the relationship in which the record was generated; the adequacy of safeguards to prevent unauthorized disclosure; the degree of need for access; and whether there is an express, statutory mandate, articulated public policy, or other recognizable public interest tilting toward access.
Various state constitutional provisions offer more protection. For one to have a claim for a violation of a constitutional privacy right, however, the individual generally must show that state action caused the violation. California's constitution (Cal. Const., Art. 1, § 1) is an exception to this general rule because it makes privacy rights explicit. California courts have held that the state's constitutional privacy provision can be asserted against private parties who infringe on citizens' privacy; see, for instance Heda v. Superior Court, 225 Cal. App. 3rd 525 (Cal., Dist. Ct., App. 1990) and Soroka v. Dayton Hudson Corp., 1 Cal. Rptr. 2nd 77 (1991). Other common law and statutory remedies, as well as institutional policies and practices, will be of greater immediate importance. This and the relevance of existing laws to HDOs is discussed in the next section.
Confidentiality
Confidentiality relates to disclosure or nondisclosure of information. Historically a duty to honor confidentiality has arisen with respect to information disclosed in the context of a confidential relationship, such as that between an individual and his or her physician, attorney, or priest. In such relationships, the confidante is under an obligation not to redisclose the information learned in the course of the relationship. Now the law applies such duties to some holders of information who do not have a confidential relationship to a patient. In the health sector, this includes such holders as utilization management firms in many states and local, state, or federal health agencies that receive reports of communicable diseases.
When one is concerned about data disclosure, whether or not any relationship exists between a data subject and a data holder, an essential construct is that of data confidentiality. Data confidentiality is the status accorded data indicating that they are protected and must be treated as such. In the federal Freedom of Information Act (FOIA, 5 U.S.C., Section 552), certain categories of data are specified as confidential and thus not disclosable; for instance, Exemption 6 states that FOIA is not applicable to ''personnel and medical files and similar files, the disclosure of which would constitute clearly unwarranted invasion of personal privacy." Data confidentiality is discussed in more detail in a later section.
Confidentiality Obligations in Health Care
Professional obligations to privacy and confidentiality. The importance of confidentiality to the medical profession is reflected in the physician's "Oath of Hippocrates." Adopted in roughly the fourth century B.C.E., it remains a recognized element of medical ethics:
Whatsoever things I see or hear concerning the life of men, in my attendance on the sick or even apart therefrom, which ought not to be noised abroad, I will keep silence thereon, counting such things to be as sacred secrets (Bulger, 1987).
In similar fashion, the American Medical Association Principles of Medical Ethics (AMA, 1992, Section 5.05) states that "The information disclosed to a physician during the course of the relationship between the physician and patient is confidential to the greatest possible degree . . . The physician should not reveal confidential communications or information without the express consent of the patient, unless required to do so by law."
Within the healing relationship, four justifications may be offered for medical confidentiality (adapted from Faden, 1993). First is a respect for privacy and patient autonomy. In the earliest practice of medicine, physicians treated patients in their homes, and medical privacy was an extension of the privacy of the home. The Hippocratic Oath, for instance, does not justify confidentiality on any ground other than respect for privacy. If information concerning a patient's mind and body are viewed as extensions of the patient, than the concept of autonomy requires that the patient be able to control disclosure and use of that information. The value placed on personal autonomy gives rise to the notion of informed consent. As Justice Benjamin N. Cardozo wrote in his opinion in Schloendorff v. Society of New York Hospital, 211 N.Y. 125, "Every human being of adult years and sound mind has a right to determine what shall be done with his body."
A second justification related to respect for privacy is the implicit and sometimes explicit expectation or promise of confidentiality. Third is the special moral character of the doctor-patient relationship, which is characterized by trust and intimacy. Confidentiality can be instrumental in fostering patients' trust in their physicians; when this trust encourages patients to speak freely and disclose information they would otherwise keep secret, it facilitates diagnosis and treatment. Fourth, respecting confidentiality protects patients from harm that might befall them if the information were to become widely available and indiscriminately used.
Legal obligations of confidentiality. Various federal and state laws impose a duty to preserve the confidentiality of personal health information. These laws can be divided into two categories: those imposing confidentiality obligations on recordkeepers and those protecting health information that is deemed highly sensitive. Examples of the former include general confidentiality statutes about health care information such as the Uniform Health Care Information Act (National Conference, 1988) and the California Confidentiality of Medical Information Act (Cal. Civil Code §§ 5656.37 [1992]), as well as various state laws and Medicare and Medicaid regulations. Laws and regulations imposing confidentiality requirements for sensitive personal health information include those related to alcohol and drug abuse records and laws governing nondisclosure of records of patients with acquired immunodeficiency syndrome (AIDS), the results of antibody tests for human immunodeficiency virus (HIV), psychiatric and developmental disability records, and information concerning results of genetics screening and testing.
Courts have also recognized a legal obligation to maintain the confidentiality of personal health care information. In response to harm resulting from unauthorized release of personal health information, courts have granted legal relief under a number of theories: breach of trust, breach of confidence, breach of implied contract, invasion of privacy, defamation, and negligence (Waller, 1992).
Disclosure of Health Information
As one looks beyond the protected sphere of the patient-provider relationship, it is not always clear who is rightly in the community of "knowers," nor is there universal agreement on principles that ought to control disclosure. With the growth of managed care, utilization review, third-party payment systems, and claims administration for self-insured health plans, information sharing for purposes of adjudicating claims and managing high-risk or high-cost cases has become part and parcel of the provision of health care. Westin has described these supporting and administrative activities as "Zone 2" in comparison to "Zone 1," which refers to information flow to support direct medical care (Westin, 1976; Harris/Equifax, 1993). These wide-ranging claims of need for sensitive health information, which are emblematic of modern health care, raise difficult problems for the preservation of privacy and maintenance of confidentiality.
Patients generally understand that, with consent, information in their medical records will be shared widely within a hospital and for insurance and reimbursement purposes. They also expect that data collected about them will be used only for the purpose of the initial collection and that such data will be shared with others only for that same purpose. Outside the health care institution, patients expect that confidential data will not be shared with people or organizations not authorized to have such information and that legitimate users of the data will not exploit such access for purposes other than those for which the information was originally obtained (e.g., see Harris/Equifax, 1993).
Consent. Such exceptions to the rule of confidentiality as described above are rationalized as being conducted by consent of the patient or a patient representative. A patient may be asked to accede to disclosure by signing a blanket consent form when applying for insurance or employment. In such cases, however, consent cannot be truly voluntary or informed. Such authorizations are often not voluntary because the patient feels compelled to sign the authorization or forego the benefit sought, and they are not informed because the patient cannot know in advance what information will be in the record, who will subsequently have access to it, or how it will be used.
Although consent may be the best-recognized way to permit disclosures of private information, consent is so often not informed or is given under economic compulsion that it does not provide sufficient protection to patients. As will be seen in the recommendations section of this chapter, this committee generally does not regard "consent" procedures as sufficient to protect sensitive information from inappropriate disclosure by HDOs, although they are a necessary adjunct to other autonomy protections.
Mandatory reporting and compulsory process. Other situations exist in which sensitive health information about individuals must be disclosed to third parties. Such sharing of health information for socially sanctioned purposes may be truly voluntary; it may also be required through mandatory reporting or coerced by court order.
Mandatory reporting requirements are justified by society's need for information; these include filing reports of births and deaths, communicable diseases, cancer, environmental and occupational diseases, drug addiction, gunshot wounds, child abuse, and other violence-related injuries. Some statutes requiring that records be retained for 10 to 25 years in some cases make past diagnoses retrievable long after they no longer accurately describe the patient. Another type of reporting requirement involves the expectation that third parties require warning about threats to their life.7
Physicians and others may also find themselves compelled to divulge patient information when they would otherwise choose not to do so. Such requirements—sometimes termed "compulsory process"—may take the form of subpoenas or discovery requests and may be enforced by court order. In some instances personal health care information may be protected from disclosure in court and administrative proceedings by virtue of the physician-patient privilege, which may be mandated by statute or derive from the common law. Information that is so privileged cannot be introduced into evidence and is generally not subject to discovery.
Weaknesses of Legal Protection for Confidentiality
Legal and ethical confidentiality obligations are the same whether health records are kept on paper or on computer-based media (Waller, 1992). Current laws, however, have significant weaknesses. First, and very important, the degree to which confidentiality is required under current law varies according to the holder of the information and the type of information held.
Second, legal obligations of confidentiality often vary widely within a single state and from state to state, making it difficult to ascertain the legal obligations that a given HDO will have, particularly if it operates in a multistate area. These state-by-state and intrastate variations and inconsistencies in privacy and confidentiality laws are well established among those knowledgeable about health care records law (e.g., see Powers, 1991; Waller, 1991; WEDI, 1992; Gostin et al., 1993; OTA, 1993; for examples ranging across many types of professionals, institutions, and ancillary personnel). This is important because some HDOs will routinely transmit data across state lines. Interstate transmission already occurs with data such as claims or typed dictation. When confidential data are transmitted across state lines, it is not always clear which state's confidentiality laws apply and which state's courts have jurisdiction over disputes concerning improper disclosure of information.
Third, current laws offer individuals little real protection against redisclosure of their confidential health information to unauthorized recipients for a number of reasons. Once patients have consented to an initial disclosure of information (for example, to obtain insurance reimbursement), they have lost control of further disclosure. Information disclosed for one purpose may be used for unrelated purposes without the subject's knowledge or consent (sometimes termed secondary use). For instance, information about a diagnosis taken from an individual's medical record may be forwarded to the Medical Information Bureau in Boston, Massachusetts (MIB, 1989; and see Kratka, 1990) and later used by another insurance company in an underwriting decision concerning life insurance. Redisclosure practices represent a yawning gap in confidentiality protection.
As a practical matter, policing redisclosure of one's personal health information is difficult and may be impossible. At a minimum, such policing requires substantial resources and commitment. With the use of computer and telecommunications networks, an individual may never discover that a particular disclosure has occurred, even though he or she suffers significant harm—such as inability to obtain employment, credit, housing, or insurance—as a result of such disclosure. Pursuing legal remedies may result in additional disclosure of the individual's private health information.8
Fourth, in some instances federal law preempts state confidentiality requirements or protections without imposing new ones. For example, the Employment Retirement Insurance Security Act (ERISA) preempts some state insurance laws with respect to employers' self-insured health plans, yet ERISA is silent on confidentiality obligations. Because 74 percent or more of employers with 1,000 or more employees manage self-insured health plans (Foster Higgins, 1991, in IOM, 1993e), such preemption is particularly troublesome.
Last, enforcing rights through litigation is costly, and money damages may not provide adequate redress for the harm done by the improper disclosure.
Security
In the context of health record information, confidentiality implies controlled access and protection against unauthorized access to, modification of, or destruction of health data. Confidentiality has meaning only when the data holder has the will, technical capacity, and moral or legal authority to protect data-that is, to keep such information (or the system in which it resides) secure (NRC/CBASSE, 1993). Data security exists when data are protected from accidental or intentional disclosure to unauthorized persons and from unauthorized or accidental alteration (IOM, 1991a).
In computer-based or computer-controlled systems, security is implemented when a defined system functions in a defined operational environment, serves a defined set of users, contains prescribed data and operational programs, has defined network connections and interactions with other systems, and incorporates safeguards to protect the system against a defined threat to the system, its resources, and its data. More generally, protective safeguards include:
-
hardware (e.g., memory protect);
-
software (e.g., audit trails, log-on procedures);
-
personnel control (e.g., badges or other mechanisms to control entry or limit movement);
-
physical object control (e.g., logging and cataloging of magnetic tapes and floppy disks, destruction of paper containing person-identifiable printouts);
-
disaster preparedness (e.g., sprinklers, tape vaults in case of fire, flood, or bomb);
-
procedures (e.g., granting access to systems, assigning passwords);
-
administration (e.g., auditing events, disaster preparedness, security officer); and
-
management oversight (e.g., periodic review of safeguards, unexpected inspections, policy guidance).
The collective intent of these safeguards is to give high assurance that the system, its resources, and information are protected against harm and that the information and resources are properly accessed and used by authorized users.
Health-Related Information
In a study that focuses on the protection of health-related data about individuals, defining which items are health related is more difficult than one might initially think. The most obvious categories are medical history, current diagnoses, diagnostic test results, and therapies. Other pieces of information are more distantly related to health—because of what one might infer about a person's health. Examples include type of specialist visited, functional status, lifestyle, and past diagnoses. Nevertheless, not everything in a medical record is relevant to health status or is health related.
Insurance coverage and marital status are cases in point. Some elements could nevertheless be considered sensitive because of the social stigma that could result if they are revealed. Examples include sexual preference, address, or the receipt of social services.
The same disclosure might be harmful to one individual but not another, or harmful to an individual in one circumstance but not in another. Personal data, particularly health-related personal data, are not inherently sensitive, but they become so because of the harmful way(s) in which they might be used. Thus, any data element in medical records, and many data items from other records, could be considered either health-related or sensitive, or both. Where the boundaries for the protection of personal health information lie is not at all obvious. In considering the actions of HDOs, this committee takes a relatively broad view of health-related data; it proceeds from an assumption that all information concerning an individual and any transactions relating directly or indirectly to health care that HDOs access or maintain as databases must be regarded as potentially requiring privacy protections.9
EXPANDED DEFINITIONS
The foregoing discussions of confidentiality are based on historical, ethical, and legal usage and have served to guide legislators and practitioners. Legally and medically, confidentiality has been treated as arising from a relationship such as that between physician and patient or attorney and client. Such usage may not be as useful to administrators, vice presidents for data processing, or system designers who must design HDO systems and are working not with relationships but with access to secondary records.
The committee suggests, therefore, that an expanded interpretation using a taxonomy that is not derived from interpersonal or interprofessional relationships might be more helpful to those responsible for protection of information in these HDOs. In this taxonomy one begins with data confidentiality, defined as the status accorded data that have been declared to be sensitive and must be protected and handled as such. The rationale for the statement about sensitivity is based on potential harm to people, potential invasion of privacy, and potential loss of entitlements or privileges.
Two consequences flow from defining data as sensitive and requiring protection. First, the data must be made secure; second, access must be controlled. As described earlier, data security includes system and network protection and assures the integrity of data-such that they are not altered or destroyed accidentally or intentionally. Some system security safeguards (e.g., control of personnel) also assure data integrity.
The second consequence of declaring data sensitive—the need for access control—is related to the concept of informational privacy described above. Access control can be operationalized by HDO planners and legislators in a form that this committee would term "information-use policy." Information-use policy in the automated system context gives rise to decisions about who can do what, with which data, and for what purpose. It leads to policymaking about who may be allowed to use health-related information and how they may use it. It also requires decisions about how health information can be used as a matter of social policy and might also include consideration of whether some data should be collected at all.
The three issues—data confidentiality, security, and information use—are obviously related (Figure 4-1) They overlap to some extent and collectively represent the area of direct concern in this report. One reason to keep the three issues separate is that different remedies are relevant to each.
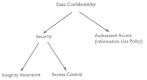
FIGURE 4-1
A new taxonomy of data confidentiality, security, and informational privacy.
Data confidentiality is a matter of law and regulation. Legislation would be required to establish that health-related information is confidential, to spell out the rationale for the position, and to clarify the ramifications and consequences of attaching protection to health data.
Security is a matter of technology, management controls, procedures, and administrative oversight. In the public sector, the action agents are regulators; in the HDO, a policy and oversight board could establish security policies. Implementation and management would be provided by technical and system design personnel.
Informational privacy (information use) is the most difficult to sort out.
The nation needs to agree on the proper use of health-related information. It is not yet clear how this will or can be done, nor is it obvious who the action agents will be. At the level of the HDO, information use would be decided by the governing board. At a regional or national level, federal agencies, legislators, professional bodies, consumer advocates, and industrial lobby groups are all likely to be involved.
In the remainder of this chapter, the terms confidentiality (rather than the more cumbersome data confidentiality), privacy (rather than informational privacy), and security continue to be used, but the committee intends that they be understood in the context just described. The committee believes this conceptualization will make it easier to translate recommendations into policies and procedures that can be implemented and enforced.
HARM FROM DISCLOSURE AND REDISCLOSURE OF HEALTH RECORD INFORMATION
Very little systematic or empirical evidence supports the widespread perception of the threat or the reality of harm from disclosure and redisclosure of health-related information. This is because the origins of the information may not be known by the person harmed, because of the natural preference not to further publicize confidential information about oneself, and because inquiry in this area has been to date more anecdotal than systematic.
This section presents examples of the potential confidentiality and privacy problems that might be encountered with health data, either in patient record form or in databases accessed or held by HDOs. Although these concerns cannot easily be quantified, reports to the committee during this study, cases mentioned in media such as the Privacy Times and the Internet-based Privacy Forum Digest, incidents known to or recounted to committee members, and similar inputs make clear that the threats and potential harm are real and not numerically trivial.
Health leader respondents to the 1993 Harris/Equifax survey showed that 71 percent were somewhat or very concerned about threats to the confidentiality of medical records, and 24 percent were "aware of violations of the confidentiality of individuals' medical records from inside an organization that embarrassed or harmed the individual." Respondents identified test results and diagnostic reports as the most frequently disclosed information.
Of the responding public, some 27 percent believed that their own medical records had been improperly disclosed. That group identified health insurers most often as having been responsible (15 percent). Fewer respondents identified hospitals or clinics (11 percent), public health agencies (10 percent), and employers (9 percent).
This section describes three categories of disclosure of patient information common today and the problems and harm that may result: (1) common disclosures that are breaches of confidentiality; (2) covert, illegal, or unethical acquisition and use of information; and (3) harm from disclosure of inaccurate data. It also raises questions about unforeseen uses of databases accessed by HDOs.
"Common" Disclosures
Three types of common disclosures pose threats: inadvertent, routine, and rerelease to third parties.
Inadvertent Release
A form of disclosure that the committee has termed "unthinking" often occurs within medical institutions. Examples include discussions with or about patients within earshot of other patients in waiting areas and discussions of cases in elevators, halls, cafeterias, and social settings. Disclosure related to the human penchant for gossip and carelessness in leaving medical records "lying around" or leaving information displayed on computer terminals is common. Westin (1972) concluded that such disclosures (sometimes to patients' relatives or friends) were less likely to be related to automated databases than to common indiscretion by hospital workers and health care providers. As the nation moves into yet more sophisticated telecommunication systems, such disclosure can include leaving detailed patient information on answering machines, sending information on fax transmissions that accumulate in common areas, or holding conversations about patients or dictating patient histories or notes about patient visits over cellular telephones.
If the diagnosis stigmatizes or indicates a disabling or fatal condition, harm can be especially serious. The harm can be great both to the famous and "VIP" patient and to noncelebrities, especially for coworkers or patients in a small community. One well-known case involved a staff physician whose HIV status became known in his hospital when his diagnosis was discussed by hospital personnel (Estate of Behringer v. Medical Center at Princeton, 249 N.J. Super. 597, 592 A.2d 1251 [1991]).
The committee believes many safeguards exist that can and should be put in place in any health care institution or HDO to anticipate and prevent disclosures of this sort. Preventing disclosure requires greater sensitivity to confidentiality issues and better training of health care workers. The Mayo Foundation, for example, has successfully developed and maintained a culture of adamant protection of the confidentiality of its patients' health information (Mayo Foundation, 1991).
''Routine" Releases or Uses in Accordance with Prevailing Practices
Health information is frequently shared without knowledge of the individual based on "uninformed" or "blanket" consent. In addition to the consent to disclose information routinely obtained from a patient before care is administered or when enrolling in a health insurance plan, another example of data disclosure is the wholesale photocopying of medical records that are forwarded to insurers, when much of the information does not pertain to the given insurance claim. The committee believes that the ability to prevent inappropriate release and use (misuse) must be strengthened. Such protections for data in HDOs are at the heart of this report and its recommendations.
Rerelease to Third Parties Without the Subject's Knowledge or Consent (Secondary Use)
The "secondary use" principle is an important component of fair information practices. It reflects the notion that when personal information is collected for a particular purpose the information should be used for only that purpose or a compatible one.10
An especially troublesome problem is the difficulty of confining the migration of information to third, fourth, or fifth parties without the individual's knowledge or consent. Examples include the sharing of health record information within organizations in one industry (e.g., between the health insurance and life insurance division of a company or between the personnel benefits division and the personnel or supervisory unit of an employer). Other examples include sharing between organizations in one industry (e.g., between the Medical Information Bureau and a second insurer). Yet a third sort of sharing can occur between organizations in two different industries (e.g., between insurer and credit bureau or between a current employer and a potential employer). A final example involves sharing genetic information with relatives who are at risk of an inherited disorder.
A major concern among commentators writing about the collection and storage of genetic information is that there will be increased pressure on the holders of such information to reveal to other patients and their physicians information gained about family members. These individuals might want to assess their own genetic risks of inheritable disease or use the information when making reproductive decisions. Some indeed have argued that there is an exception to physician duties of confidentiality analogous to that of duties to warn (or protect) people at risk from those with psychiatric disorders or HIV infection.
Given the growth in fringe benefits offered by employers and their subsequent stake in managing the costs of such benefits, there are few limitations on information that can be gathered for use in administering health, disability, and pension plans. Committee members were told repeatedly that self-insured employers are given access, when they insist, to patient-identified health claims information. Indeed, some third-party administrators (TPAs) provide human resources personnel with dial-in capability to perform their own analyses of data concerning a firm's employees and dependents (personal communication, third-party software and services vendor, 1993). Whether employers have the right to data incident to the health care for which they have paid is highly debatable, but this rationale is commonly accepted by TPAs under the pressure of competition, and there is great risk that data will not be partitioned from use in personnel actions. The 1993 Harris/Equifax survey confirmed the public's concern about this problem. Forty percent were somewhat or very concerned that their job might be affected if their medical claims information was seen by their employer. Another example of information that is in some ways mandated and also creates a database of problematic information is that which is compiled by medical review officers in connection with employee drug-testing programs.
Although corporate and professional ethics tend to discourage abuse, few barriers exist to an employer's use of its employees' medical and insurance claims records. The threat of liability under the Americans with Disabilities Act has served as a brake on some employers' access to and use of their employees' health records. In addition, some state laws limit access. Employers, however, may be required by federal or state regulations to access records in order to identify employees who pose threats to security. Information available under such permission may pertain to spouses and dependents as well as employees.
The committee believes secondary use of medical information by employers is common and may be increasing as employers seek to find ways to manage high-cost cases, to adjust their benefit packages to control their health care exposure,11 and perhaps even to identify or terminate high-cost employees or those with high-cost dependents. Real or potential harm ranges from the inconsequential to the calamitous. It is likely that the ability to limit secondary use can be strengthened, and ways to accomplish this are at the heart of the committee's concerns.
Covert Acquisition and Use of Data for Illegal or Unethical Purposes
Another problem involving acquisition and use of medical information occurs covertly through illegal or unethical means. Examples include information brokers who tap into computerized systems by using false names or by bribing database employees to supply information about celebrities or the names of individuals with certain characteristics. In health care institutions, there is also a risk that employees will browse through medical records out of curiosity (as tax and credit bureau employees have done).
The character of the threat to confidentiality posed by the aggregation of databases is altered. Celebrities have long been vulnerable to loss of privacy through both paper and computerized searches as documented by Rothfeder (1992). The new vulnerability posed by computerized searches is to those who until now have been (relatively) anonymous. That is, information brokers seek to identify information not about an identified individual but about the identities of individuals with given characteristics (e.g., those with a diagnosis of AIDS or women who have had an abortion).
Isikoff (1991) describes the growth of the information-broker industry, which boasts instant access to a range of confidential computer data—credit reports, business histories, driver's license records, Social Security records, and criminal history backgrounds. Some of these records are public, but some are in government and private computer databases; in the latter, illegal access may involve insiders (e.g., employees of the Social Security Administration, police and other law enforcement employees). Of particular concern is the problem of unauthorized disclosure by often low-paid individuals who have legitimate access to information but who use it to facilitate illegitimate searches or to profit from the sale of records—a practice some have termed "insider information trading" and known to data system security specialists as the "insider threat."
Hendricks (1992) described a recently published hacker's manual for penetrating TRW's credit bureau database; it was complete with dial-up numbers, codes, and methods for persuading credit bureau subscribers to divulge their passwords over the phone. He described how the traditionally youthful hackers have been supplanted by profit-oriented criminal enterprises and the emergence of individuals who, in this case, proclaim the right of the individual to conquer and destroy the "system" and its laws and to damage individuals for excitement and profit. Those who are determined to break into a system can be thwarted only with thoughtful and comprehensive system safeguards.
Although harm from this source is likely to occur rarely in comparison with others, the harm can be great because so many individuals are affected. Further, the data holder can be severely damaged in the public's eye. One goal for an HDO must be to assure the public of reasonable, if not absolute, safety.
Release of Inaccurate Data
A different harm can result from release of information when data are incomplete, inaccurate, or out of date. Examples are medical records or insurance claims on which diagnoses are listed or coded incorrectly (e.g., mastectomy for myringotomy). Other problems involve diagnoses that were considered at one time and ruled out but are still listed as a final diagnosis, incorrect inferences drawn from diagnostic tests, and clinical distortions that result from coding limitations. Data inaccuracies also arise from actions that are intended to be beneficial—for example, to protect the patient from a stigmatizing diagnosis, to permit insurance reimbursement for a test or procedure that might otherwise not be covered (as in the case of preventive and screening tests), or to allow a frail patient to be treated on an inpatient rather than outpatient basis.
The committee does not know how often these irregularities occur. Studies of the accuracy of medical records consistently show unintentional and sometimes intentional errors (Burnum, 1989), and medical records personnel and researchers report that errors and omissions are extremely common in all health records. Harm from such problems may range from trivial to severe. Any reliance on databases for such social benefits as credit ratings or life insurance means that data that are incomplete, inaccurate, or false (for example, when records of several different people are combined) are not merely useless, they are pernicious. Such errors and omissions were not a major focus of the study committee. It should be noted, however, that the converse of this problem is that the more accurate and comprehensive the databases, the more pressure there will be for access, which in turn raises the chances of harm in the other categories already discussed.
Harm resulting from inaccurate or out-of-date data can be mitigated or prevented in a number of ways, including adequate and regular attention to the reliability and validity of database contents as described in Chapter 3. Allowing individuals to obtain, challenge, and correct their own records can also help to improve their accuracy.
PRIVACY INTERESTS AND HDOs
HDOs may pose a threat to privacy interests in four ways. The first arises through harm from secondary use. This includes the potential for stigmatizing and embarrassing patients; adversely affecting their opportunities for employment, insurance, licenses, and other benefits; undermining trust and candor in the health care provider-patient relationship; and defeating patients' legitimate expectations of confidentiality. Second is the unpredictable effect that will be produced by the mere existence of HDOs as described. Third, HDOs may exacerbate societal concerns about the emergence of national, centralized personal record databases, which may be perceived as a national identification system or dossier. Issues concerning the Social Security number and its analogs are especially pertinent here. Finally, HDOs will need to be mindful of the possible effect that research uses may have on privacy.
Foreseen and Unforeseen Circumstances
In addition to the current risk of breaches of confidentiality and the risk of harm from inaccurate data inherent in the paper record, the existence of any accumulation of valuable data will spawn new users, new demands for access, and new justifications for expanded access.
HDOs may unintentionally create a heightened risk of disclosure resulting with the new forms of data becoming available through the HDOs, new inquiries and types of inquirers, new uses, and new legal and governance structures. The mere presence of the HDO may, over time, encourage new practices or changes that may be harmful to at least some segments of the population.
HDOs must also realize that the more information it holds or can access, and the more valuable that information, the greater the temptation will be for others to acquire and covertly use the information. An HDO database becomes, in some sense, like a swimming pool or an abandoned refrigerator to a child-an overwhelming opportunity or, in legal terms, an attractive nuisance.
Computerization poses problems for the protection of privacy and confidentiality, but it also offers new opportunities for protection. For example, access to records and to defined parts of records can be granted, controlled, or adapted on a need-to-know (or function-related) basis; this means that users can be authorized to obtain and use only information for which their access is justifiable. It will also be possible to implement authentication procedures (discussed below) and to implement and publicize the use of methods to permit the HDO to know if anyone has browsed in the databases, who has done so, and which data were accessed. Automation could also greatly mitigate the disclosure that now occurs when, for instance, an entire medical record is copied to substantiate a claim for a single episode of care, and software could prevent the printing or transfer of database information to other computers.
A National Identification System or Dossier
Privacy advocates can be expected to express sharp concerns about the potential for HDOs to be linked with one another or with other types of personal databases such as the financial, credit, and lifestyle databases maintained by consumer reporting agencies and information services. One particular threat is the possible contribution of linked databases to development of a de facto national identification (and data) system. Such a system would comprise a comprehensive, automated dossier on virtually every citizen.
Conventional wisdom holds that after a personal information database is established, some consequences are inevitable (Gellman, 1984): expansions in permissible uses of the database; demands to link the database with complementary databases to improve the database product; and relaxations of confidentiality restrictions. With respect to HDOs, privacy advocacy groups and the media are likely to be concerned that over time various regional HDOs will establish telecommunications links and that these entities will become a national network linkable to other financial and government records such as those serving the Social Security Administration or the Internal Revenue Service.
As potential users of HDO data files, many persons in these groups might regard this scenario as desirable and beneficial; as potential record subjects, however, most would probably be uncomfortable with this threat to their privacy. Once such a system were in place, some fear that both those with and without bona fide access would be able to call up a remarkably comprehensive and intrusive dossier comprising detailed biographic information, family history information, employment information, financial and insurance information, and, unless prevented, of course, medical record information about every citizen participating in the system.
In the view of many, this development would bring the nation perilously close to a national identification database. Indeed, at that point the "national" network would lack only a means of positive identification and a requirement that all citizens participate to constitute such a national identification system.12 HDOs will need to take steps to be certain that they do not contribute to these developments.
Although many people carry credit or health insurance cards and have no objection to doing so, others would view any requirement that a special identification card must be carried by participating consumers with special alarm because such an instrument is thought to connote totalitarian values. In the former Soviet Union, for instance, all Soviet citizens were required to carry an internal passport and to produce this passport upon request. In this way, the passport served not only to regulate internal travel but as a means of identification and social control (Pipko and Pucciarelli, 1985). The Harris/Equifax survey found that the great majority of the public (84 percent) is willing to accept a personal identity card but had mixed feelings about being assigned a number—perhaps reflecting concern about whether such a number could be used to link their health information to other databases.
Admittedly, a few Western democracies employ national population registries and automated and centralized personal record data banks, but virtually all these systems are principally statistical and research systems, rather than systems that are used for administrative or investigative purposes. Moreover, even these primarily statistical and research systems "inspire fears about the expanded power of central government, vis-à-vis the legislature, the local administration, the private sector and most especially the citizen" (Bennett, 1992, p. 49). In Sweden, for example, the press harshly criticized the linkage of cancer registry databases and abortion record databases for medical research purposes (Stern, 1986).
Moreover, European democracies that use unique personal identification numbers assigned at birth for each citizen have a history of the use of personal, numerical codes. Even in Sweden and Germany, two European democracies that make extensive use of personal identification numbers to track individuals and link databases, personal identification numbers are not used as a standard universal numeric identifier for participation in all aspects of the society. In addition, reports are increasing of popular resistance in these countries to the use of universal numeric identifiers (Stern, 1986). As Bennett (1992) comments in Regulating Privacy:
The issue in these countries [Sweden and Germany] has been the incremental and surreptitious use of these numbers for ends unrelated to those for which they were created. Where proposals have been introduced for a new universal identifier accompanied by a personal identification card, such as in Germany and Australia, they have been met with strong resistance because of the belief that non-uniformity and non-standardization with all the attendant problems for administration, are vital to the maintenance of personal privacy. (p. 51)
Over the years the Congress, the press, and privacy advocates have fiercely resisted any proposal for the development of databases that appeared to facilitate establishment of a national identification or database system.
Some observers urge that entities like HDOs eschew the use of any type of positive identification, such as a biometric identifier, and avoid the use of the Social Security number. The aim is to minimize the likelihood that HDOs will contribute intentionally or unintentionally to a national identification system or to the development of a standard universal identifier (USDHEW, 1973). If the HDO initiative is viewed by opinion leaders as a precursor to the establishment of any type of automated, national identification or dossier system, the initiative will likely fail.
HDO proponents should take every practicable step to assure advocacy groups, the media, legislators, and the American people that the emergence of HDOs will not contribute to the development of a centralized, automated national dossier system or a national identification system through linkage with non-health-related databases or the gradual relaxation of confidentiality policies.
Personal Identifiers and the Social Security Number
The personal identifier (ID) used by an HDO to label each of the individuals in the database is a crucial issue. It is related not only to past practices but will also be strongly influenced, if not mandated, by the health care reform actions now under way in the nation.
Of necessity, identifiers are used in present health care systems. For practical purposes the identifier in many systems is either the person's Social Security number (SSN) or, as in Medicare, the Social Security number of an individual with a letter appended. Issues relating to the Social Security number are examined below (see also USDHEW, 1973).
An Ideal Personal Identifier
The ideal personal identifier must, whatever its design, minimize or eliminate the risk of misidentification. An ideal identifier would meet certain requirements, including the six discussed below.
First, it must be able to make the transition easily from the present recordkeeping environment to one that will prevail in HDOs (and under national health care reform). Further, organizations will need to know where to apply for new numbers, to verify numbers that patients give verbally, to track down uncertainties in identification, to find current mailing addresses, and to be able to backtrack errors and correct them. This requirement also has technical dimensions. For example, if a new identifier contains more digits or characters (or both) than the 10 used for the Medicare identifier, there will be software repercussions in many systems, and redesign of data-capture forms may be necessary.
Second, the identifier must have error-control features to make entry of a wrong number unlikely. Control implies that errors of many kinds are detectable and possibly correctable on the basis of the digits and characters in the ID alone. Ideally it will protect against transpositions of characters and against single, double, or multiple errors. At a minimum the error-control features must be able to indicate whether the ID is valid and to do so with high confidence (USDHEW, 1973).
Error control is certain to be a system-wide requirement in any automated system. It will involve not only the structure of the ID itself, but also the processing software (or the residual manual processes) in every system that will have to use and verify the ID.13
Third, the ID will have separate identification and authentication elements. The distinction between identification and authentication is made where strong security is required. "Identification" implies that (in this case) an individual indicates who he is, but authentication is a separate process with different parameters (known only to the individual) that allow the system to verify with high confidence that the identification offered is valid. Banks, for example, sometimes require an individual to provide his mother's maiden name; a personal identification number (PIN) is another authenticator. In many, perhaps most, medical systems this distinction is not made, and a simple identifier (e.g., insurance plan identification number) is presumed to be correct. In the future, however, some consideration should be given to separating these functions.
- 1.
-
Identifying that something is wrong, but not indicating the error,
- 2.
-
Detecting and locating a single error,
- 3.
-
Detecting and locating multiple errors,
- 4.
-
Detecting, locating, and correcting single errors, and
- 5.
-
Detecting, locating, and correcting multiple errors.
The number of additional characters needed depends on the degree of error detection and correction that designers think is necessary for the circumstances. For example, a single check digit can identify an error but does not locate which digit is wrong or how. Moreover, it would not catch the common manual error of transposed characters. A simple single-digit check can sometimes say a bad message is good. For such reasons, a single check digit is not a very strong error control mechanism.
The issue of designing error codes becomes complex rapidly. It is essential, however, to realize that any error correction feature added to an established number such as the SSN will have hardware and software consequences—or both. The data fields in storage will have to be longer; the software will have to be modified to handle the longer data fields; additional software—or hardware or both—will have to be added to do whatever calculations the particular error-detection/correction scheme requires.
Error control is a system-level problem, not just an issue of the identifier per se. If one can arrange procedures so that the identifier is always known to be correct at the time it is entered into the automated system, then the problem within the system itself becomes simpler. The method of providing the identifier will result in higher or lower assurance of its accuracy: an individual's memory is probably the least assurance of correctness; an embossed card is better; and an electronic reader for the card is better still.
The present health care information infrastructure runs largely without external visible error controls. Although mainframes and communications equipment almost certainly have error controls to catch equipment malfunctions and communication faults, there is no error control on some, possibly much, of the data in the data base. It relies, instead, on people outside the system to detect errors—providers and patients—and risks major mistakes in processing.
Fourth, the ID must work in any circumstance in which health care services are rendered, whether or not the situation was anticipated in the design of the system. At a minimum, the ID must never be an impediment to the prompt, efficient delivery of health care. For example, it must work when the patient requiring health care is not able to cooperate (e.g., is unconscious or does not speak the same language as the health care personnel) and regardless of the patient's mental and physical abilities.
Fifth, the ID must function anywhere in the country and in any provider's facilities and settings. By extension, it must also be able to link events that have occurred at multiple providers.
Sixth, the ID must help to minimize the opportunities for crime and abuse and perhaps help to identify their perpetrators.
Issues Relating to the SSN
When the initial Social Security law was passed in 1935, the SSN was called the SSAN, the number of one's "account" with the Social Security Administration (SSA). The SSA has always held that the SSN is not to be used as a personal identifier.14
In 1943 President Franklin Roosevelt signed an executive order requiring federal agencies to use the SSN whenever a new record system was to be established. The Department of Defense adopted it as a military identification number during World War II, and in 1961 the Internal Revenue Service (IRS) adopted it as the taxpayer identification number. When Medicare legislation was passed in the 1960s, the government adopted the SSN plus an appended letter as the Medicare health insurance number. Many experts regard this as a serious undermining of privacy protection because the many recordkeeping activities associated with health care delivery act to disseminate a piece of information that differs from the SSN by only an appended letter.
In the Privacy Act of 1974—largely in response to the position of a Department of Health, Education, and Welfare (USDHEW, 1973) committee that had studied the issue—Congress prohibited states from using the SSN for enumeration systems other than by authority of Congress; however, states already using it were allowed to continue. The Tax Reform Act of 1976 undermined this position, however, by authorizing the states to use the SNN for a variety of systems: state or local tax authorities, welfare systems, driver's license systems, departments of motor vehicles, and systems for finding parents who are delinquent in court-imposed child-support payments (OTA, 1986).
In short, the government has caused the proliferation in the use of the SSN, sometimes by positive actions but sometimes by indifference or congressional failure to act. Some government decisions, notably to use the SSN as the taxpayer identification number and as the basis of the Medicare number, forced its wide diffusion throughout the private sector through financial transactions and benefits payments. In this way—partly deliberately and partly inadvertently—a very sensitive item of personal information has become widely disseminated.
SSN Uses for Other Than Medical Payments
Organizations that use the SSN as a personal ID and that most citizens will deal with frequently include federal government agencies (e.g., the Social Security Administration for benefits, the Internal Revenue Service for taxes and withholding, the Health Care Financing Administration and its contractors for Medicare payments, and the Securities and Exchange Commission); educational institutions, which frequently use it as a student identifier for campus-wide purposes; state governments (e.g., for state taxes, property and other local taxes, driver and vehicle registrations, real property records, financial transactions, and Medicaid payments); and private organizations (e.g., providers for health care services, industry-support databases such as the Medical Information Bureau, mortgage and loan agencies, credit reporting organizations, real property records, and banks).
Organizations, especially those in the private sector, choose to use the SSN for a number of pragmatic reasons and for expediency. Organizations already hold the number legally in connection with tax, financial, and wage matters. Moreover, there are no prohibitions against its use as a personal identifier in the private sector. Individuals usually have an SSN, or they can get one easily. In addition, people have become accustomed to willingly providing an SSN when asked; hence, its acquisition is a matter of merely asking, not legal compulsion.15 Finally, administration of an enumeration system can be burdensome, and the choice of SSN shifts that consequence onto the government.
Although federal, state, or local governments usually require the SSN under law, private-sector requests serve the purposes and motivations of the organization. The essential point is that the SSN is in extraordinarily wide use as a personal identifier. As a result, any given person is indexed in a huge number of databases by his or her SSN, and an unknown number of linkages and data exchange among such databases are routine business.
If health care reform were to mandate a patient ID that is either the SSN or a closely related number, it will in effect have forced the last step of making the SSN into a truly universal personal ID. This is the issue that launched the DHEW committee in 1970 (PPSC, 1977a).
Shortfalls of the SSN as an Identifier
The choice of a personal ID that is satisfactory for the operational needs of health care delivery, but at the same time assures the confidentiality of medical data and the privacy of individuals is neither easy nor casual. Superficially, the choice would be the SSN, Medicare number, or something similar simply because people are accustomed to using them, systems are used to handling them. The government would bear the burden of administering the enumeration system but would avoid the cost of creating a new one. For information management, however, the shortfalls of the SSN are well known. The following list is representative of the problems.
- 1.
-
Any 9-digit number rendered with hyphens in the appropriate places—that is, XXX-XX-XXXX—has a high likelihood of being a legitimate SSN that belongs to someone or at least appears to. This provides little security, and data commingling can occur that would result in erroneous records, mistaken conclusions and actions, and incorrect payments.
- 2.
-
The allowable entries in each of the three groups in a SSN are well known. Thus, it is easy to counterfeit an SSN and have a high probability that it will not be challenged.
- 3.
-
It has no error correcting features. It is fallible to transpositions and single- or multiple-digit mistakes.
- 4.
-
The SSN is not coupled to an authenticator. Some organizations, such as banks, attempt to provide such a feature by using some ad hoc data element that an individual is likely to remember but is not common knowledge (e.g., mother's maiden name).
- 5.
-
The SSN circulates widely, particularly in the finance industry. It is relatively easy to acquire someone's number and to parlay it into a false identity that supports fraud or other malicious or illegal actions.
- 6.
-
There are often multiple holders of the same SSN, which introduces errors and clouds the records. Especially among less well-informed or immigrant households, the purpose of the number is not well understood or is colored by the role that a number might have played in another country or society. For example, all members of a household might use the same SSN because they believe it is intended to apply to all of them. Some numbers have achieved very wide use. The most famous is the ''wallet incident" in which a replica of an SSN card complete with a number was included in an inexpensive, widely sold wallet; an appreciable number of people improperly believed that this SSN was to be used.
- 7.
-
The SSN is closely related to the Medicare identifier, which identifies virtually all members of the population over age 65. For married people who receive SSA Title II benefits paid to an individual and the spouse on the basis of one person's earnings, the Medicare number of the primary beneficiary is the SSN followed by an A; for the spouse, the Medicare number is that same SSN followed by a B.
- 8.
-
Not everyone needing health care has an SSN; for instance, foreign visitors, newborn infants, and the indigent or homeless are all likely to lack SSNs. This would require that health care providers be prepared to assign substitute numbers.
- 9.
-
The crucial, almost overwhelming, objection to the SSN as a medical identifier, however, is that it has no legal protection, and because its use is so widespread, there is no chance of retroactively giving it such protection. As a data element, it is not characterized by law as confidential; hence, organizations that use it are under no legal requirement to protect it or to limit the ways in which it is used. For all practical purposes its use is unconstrained, this makes the risk of commingling health data with all other forms of personal data enormously high.
Confidentiality of Research Uses of HDO Databases
Through expenditures for medical research, the government and private sector indirectly contribute to third-party intrusions. Although epidemiological research was originally concerned with the causes and prevention of infectious diseases and focused chiefly on populations, such research has expanded to include chronic, noninfectious diseases with low rates of occurrence (PPSC, 1977a). Progression of such ailments may be slow, and because their causes are frequently insidious, their study often requires medical surveillance of a substantial population at widely disparate times.
In some cases, HDOs may serve research and statistical uses, and this raises consideration of how privacy interests might be affected. First, the benefits of such databases generally accrue not to the individual data subject but to society; this makes assessments of risks and benefits more complex because the person at risk is not the same as the beneficiary. Second, research databases depend on the voluntary cooperation of subjects, providers, or both in providing accurate and reliable information. If patients or clinicians distrust the ability or willingness of HDOs to protect the confidentiality of information, they may intentionally withhold or distort information. Third, it will become extremely important to understand the implications of differing methods of data collection and sources of data—for instance, abstraction of primary records and analysis of claims databases compared with patient responses to surveys fielded by the HDO. Each will have different sources of bias in the population reached, reasons for missing data, and accuracy.
With respect to research and statistical studies, Congress and agencies of the federal government have acted to protect the interests of individuals who are subjects of research and statistical records developed under federal authority or with federal funds (PPSC, 1977a). A report from the National Research Council (1993) analyzes available technical and administrative procedures that can be taken to protect confidentiality of data while permitting legitimate data use. A number of such disclosure limitation techniques are described: (1) collecting or releasing a sample of the data; (2) including simulated data; (3) "blurring" of the data by grouping or adding random error to individual values; (4) excluding certain attributes; (5) swapping of data by exchanging the values of certain variables between data subjects; (6) requiring each marginal total of the table to have a minimum count of data subjects; (7) using a "concentration rule" (described in Chapter 3); and (8) using controlled rounding of table entries (NRC, 1993). Whether these steps are sufficient in the HDO context requires reexamination.
Because HDO databases will include many elements of personal information collected for single, specific purposes and subsequently used for multiple, diverse purposes, they have the potential to conflict with the secondary use principle. If such secondary use does not, however, involve a decision about the individual, then the privacy threat is by no means as acute as it would be if the information were used to make a decision directly affecting the individual (USDHEW, 1973). Individuals' interests have not been compromised, for example, when these data are used anonymously for statistical or research purposes and not for administrative decision making that will affect them directly. Although the Harris/Equifax survey (1993) found that respondents objected to such use of their medical information without their express consent (64 percent of respondents), the IOM committee believes that individuals—and collectively, the public—may need to better understand the benefits of health services research using non-person-identifiable data and protections that are available for research use of person-identifiable data. Researcher access to HDO databases is addressed in the committee's recommendations.
RELEVANCE OF EXISTING LAWS TO HDOs
The committee examined existing law-constitutional, statutory, and common law-for its relevance to HDOs and its adequacy for protecting patient privacy. The committee also examined the way these laws might affect the design, establishment, and operation of HDOs.
It concludes that most of this body of law is unlikely to apply to HDOs. With the exception of laws regulating information considered sensitive, existing laws regulate recordkeepers and their recordkeeping practices; they do not regulate on the basis of either the content or the subject matter of a record. Current law thus seeks to regulate the information behavior of health care providers, government recordkeepers, insurers, consumer reporting agencies, quality assurance organizations, and researchers. For this reason, it is important to understand how HDOs are likely to be viewed by the legal system-that is, in what legal context their recordkeeping will be seen.
The committee believes that HDOs are unlikely to be treated as health care providers, payers, or quality assurance organizations. If they are treated as medical researchers, very little in the way of standards would apply. Some possibility exists that they will be subject to regulation as consumer reporting agencies—and they will probably want to avoid this—or as insurance support organizations, at least in states that have passed The National Association of Insurance Commissioners (NAIC) Information and Privacy Protection Model Act of 1981 (NAIC Model Act). Implications of being treated as either are described briefly below. HDOs may well have governmental status, and the legal implications of that status are described in more detail, with particular attention to the Privacy Act of 1974.
Laws Governing Insurance Support Organizations
The NAIC Model Act defines an insurance support organization as "any person who regularly engages, in whole or in part, in the practice of assembling or collecting information about natural persons for the primary purpose of providing the information to an insurance institution or agent for insurance transactions" (emphasis added). Because HDOs will likely provide information to insurance institutions on a regular basis in connection with insurance transactions (defined in the NAIC Model Act as a determination of an individual's eligibility for insurance coverage, benefit, or payment), it is possible they will be considered insurance support organizations.
In states that have passed the NAIC Model Act, an HDO would be subject to the following six requirements. First, the HDO could not disclose personal information about an individual without the written authorization of the individual or unless the disclosure was needed: to further an insurance function, provided there is no redisclosure; to a health care institution or health professional; to an insurance regulatory authority; to a law enforcement authority; in circumstances otherwise permitted or required by law; in response to compulsory process; for the purpose of a bona fide research study, provided that no individual can be identified in any subsequent research report; for marketing purposes; to consumer reporting agencies; to a group policyholder; to a professional peer review organization; or for a licensing activity.
Second, when subject consent is obtained, the HDO would have to assure that the consent has several properties: that it (1) is written in plain language; (2) is dated; (3) specifies the types of persons authorized to disclose information; (4) specifies the nature of the information authorized for disclosure; (5) names the institution authorized to disclose; (6) specifies the purposes for which the information is being disclosed; (7) specifies the length of time for which the authorization is valid; and (8) advises the individual whose information is the subject of the consent that the individual has a right to a copy of the consent form.
Third, the HDO would have to provide record subjects with a right of access to their records, either directly or through a health care professional designated by the individual. Fourth, the HDO would be required to provide individuals with rights of correction, amendment, and deletion. Fifth, the HDO could not maintain information concerning any previous adverse underwriting decision relating to the individual. Sixth, the HDO would be subject to the regulatory and investigatory powers of the state commissioner of insurance.
In states that have not adopted the NAIC Model Act, there is little or no statutory regulation of the information practices of insurance institutions or insurance support organizations (Trubow, 1991) to apply to HDOs. In theory, the above requirements might not apply at all in those states, or they might apply piecemeal by virtue of state-specific situations.
Laws Governing Consumer Reporting Agencies
It is possible, but by no means likely, that HDOs could be viewed as consumer reporting agencies under the federal Fair Credit Reporting Act (FCRA) or state versions of the FCRA. These statutes regulate the collection, use, and dissemination of personal information by consumer reporting agencies. Federal law defines a consumer reporting agency as an organization that "regularly engages in whole or in part in the practice of assembling or evaluating consumer credit information or other information on consumers for the purpose of furnishing consumer reports to third parties" (FCRA 15 U.S.C. § 1681a[f]) for fees or on a cooperative, nonprofit basis. "Other information on consumers" includes medical record information.
The FCRA defines "consumer report" as any written or oral communication that bears on consumers' credit worthiness, credit standing, credit capacity, character, general reputation, personal characteristics, or mode of living when that report "is used or expected to be used or collected in whole or part for the purpose of serving as a factor in establishing the consumer's eligibility for: credit or insurance to be used primarily for personal, family or household purposes" or used "in connection with a business transaction involving the consumer'' (FCRA 15 U.S.C. §§ 1681a(d) and 1681b(3)(E)).
If data from an HDO are used only in connection with insurance claims determinations, the HDO should not, at least by virtue of the insurance claims function, be classified as a consumer reporting agency. The Federal Trade Commission (FTC), which is charged with enforcing the FCRA, has stated that supplying data for insurance claims purposes does not constitute a consumer report.
If, however, HDOs were to acquire and supply personal financial information to health care providers to assist providers in making determinations about a patient's payment of a medical bill (including the acceptance of a consumer's credit card or check or the allocation of charges between the patient and various health care payment programs), HDOs would be providing information for use "in connection with a business transaction involving the consumer." Courts have held, for example, that providing financial information for point-of-sale determinations of whether to accept a consumer's check represents a disclosure in connection with a business transaction involving a consumer. This kind of action brings the party making the disclosure within the scope of the FCRA.
If, though highly unlikely, the FCRA were judged to be applicable to HDOs, then they would be subject to its provisions. These include limitations of the kind of personal information that could be collected and maintained; requirements with respect to consumer access to the database; restrictions on the disclosure of the information from the database; and a variety of administrative, civil, and criminal sanctions. Given the reach of the FCRA, the committee judged that HDOs will want to avoid action and responsibilities that will put them within the purview of the FCRA.
HDOs as Governmental Entities: General Confidentiality Protections in Public Law
The governmental or private status of an entity that maintains or uses personal record information is particularly significant for recordkeeping. Constitutional principles, legislative charter, statutory law, and regulations must be considered separately.
Constitutional Law
If an entity has a governmental status, whether federal or state, constitutional privacy standards apply to the entity's handling of personal information. As noted earlier, various provisions of the U.S. Bill of Rights are aimed at protecting citizens from governmental abuse, and privacy rights are derived from limited case law (e.g., Whalen v. Roe). For federal or state constitutional protections to apply, an HDO would have to be operated by a governmental entity or pursuant to a governmental charter.
Legislative Charter
Even if HDOs are not operated by federal governmental entities, constitutional information privacy standards can affect their operations in two ways. First, HDOs may well operate under a state legislative charter. If that charter were to require the submission of personally identifiable medical record information (on the part of record subjects, providers, or others), this statutory requirement provides a basis for a challenge on constitutional privacy grounds, just as did the reporting requirements in Whalen.
Second, even if the HDOs are not statutorily chartered, constitutional information privacy concepts are used by the courts as benchmarks for assessing whether a privacy violation has occurred under common law or statute. Accordingly, if an HDO were challenged on tort or other common law or even statutory privacy theories, the extent to which the HDO violates constitutional informational privacy rights could well be influential in determining the outcome.
Freedom of Information Acts
In addition to any constitutional protections (which will be limited at best), a body of statutory law would also apply to HDOs if they were considered to be public agencies. For example, federal agencies and agencies in every state are covered by freedom of information (FOI) or public records acts. These statutes are intended to make records held by government agencies available to the public. The federal FOIA, however, contains express language that exempts from disclosure "personnel and medical files and similar files the disclosure of which would constitute a clearly unwarranted invasion of personal privacy" (5 U.S.C. § 552[b][6]). Most state freedom of information statutes include a similar exemption. Washington State's FOIA, for example, includes an exemption for medical records, pharmacy records, client records held by domestic violence programs, and various types of research data. The Washington courts have also held that medical records are exempt from disclosure under Washington's FOI statute.16
Fair Information Practices
In addition, the federal government and approximately one-third of the states have adopted fair information practices and statutes covering governmental agencies within each jurisdiction. The federal Privacy Act prohibits federal agencies, or contractors acting on behalf of an agency, from disclosing information accessible by personal identifiers and contained in a system of records without the prior written consent of the individual concerned.17 The federal government and states that have adopted comprehensive privacy laws are also required by statute to make records relating to a record subject available upon request to that individual. Federal agencies and those in some states can, however, adopt special procedures that bar direct access to medical record data when officials have reason to believe that such access would be harmful to the subject (Cleaver, 1985; Andrussier, 1991).
The right to know about, challenge, control, and correct information about oneself are hallmarks of American privacy law. The elements of fair information practices derive from the report of the Secretary's Advisory Committee on Automated Personal Data Systems (USDHEW, 1973). The five principles in the original code are enumerated in that report (p. 41) as a Code of Fair Information Practices:
- 1.
-
There must be no personal data recordkeeping systems whose very existence is kept secret.
- 2.
-
There must be a way for an individual to find out what information about him is in a record and how it is used.
- 3.
-
There must be a way for an individual to prevent information about him obtained for one purpose from being used or made available for other purposes without his consent.
- 4.
-
There must be a way for an individual to correct or amend a record of identifiable information about him.
- 5.
-
Any organization creating, maintaining, using, or disseminating records of identifiable personal data must assure the reliability of the data for their intended use and must take reasonable precautions to prevent misuse of the data.
The Privacy Act of 1974. The Privacy Act of 1974 (P.L. 93-579; 5 U.S.C. § 552a) concerns databases held by the federal government.18 Along with FCRA and the Family Educational Rights and Privacy Act of 1974, this act invests record subjects with rights to see, copy, and correct their records, as well as with limited rights with respect to authorizing the collection and disclosure of information.
The Privacy Act of 1974 incorporated the five elements of the Code of Fair Information Practices as eight principles that are manifest as specific requirements (PPSC, 1977a):
- 1.
-
There shall be no personal data recordkeeping system whose very existence is secret and there shall be a policy of openness about an organization's personal data recordkeeping policies, practices, and systems (The Openness Principle).
- 2.
-
An individual about whom information is maintained by a recordkeeping organization in individually identifiable form shall have a right to see and copy that information (The Individual Access Principle).
- 3.
-
An individual about whom information is maintained by a recordkeeping organization shall have a right to correct or amend the substance of that information (The Individual Participation Principle).
- 4.
-
There shall be limits on the types of information an organization may collect about an individual, as well as certain requirements with respect to the manner in which it collects such information (The Collection Limitation Principle).
- 5.
-
There shall be limits on the internal uses of information about an individual within a recordkeeping organization (The Use Limitation Principle).
- 6.
-
There shall be limits on the external disclosures of information about an individual a recordkeeping organization may make (The Disclosure Limitation Principle).
- 7.
-
A recordkeeping organization shall bear an affirmative responsibility for establishing reasonable and proper information management policies and practices that assure that its collection, maintenance, use, and dissemination of information about an individual is necessary and lawful and the information itself is current and accurate (The Information Management Principle).
- 8.
-
A recordkeeping organization shall be accountable for its personal data recordkeeping policies, practices, and systems (The Accountability Principle).
In addition to establishing privacy guidelines for federal databases, the Privacy Act also created the Privacy Protection Study Commission (PPSC), whose charter required it to examine recordkeeping practices in the private business sector and in selected federal domains (e.g., tax records). The PPSC revisited the Fair Practices doctrine and reoriented the thrust of the Fair Practices somewhat by placing emphasis on promoting consent and participation rights, which it referred to as "fairness protections for individuals" (PPSC, 1977a, pp. 17-18). In fact, the majority of the commission's recommendations relate directly to fairness in recordkeeping. In the case of an individual, essential fairness protections include a right of access to records about oneself for reviewing, copying, and correcting or amending them as necessary, plus some control over the collection and disclosure of information about oneself.
The PPSC offered an illustrative revision of the Privacy Act to incorporate changes it suggested in its report. These modifications included steps in the following areas: amending records; limitations on disclosure; collecting and maintaining information; "propagating corrections" (which involves taking positive steps to correct information); uses for research or statistical records; notices about agency systems; policies and practices; rights of parents and legal guardians; agency implementation; civil remedies and criminal penalties; application to government contractors and grantees; archiving records; giving notice of new systems or alterations to old systems; reporting to the U.S. Congress; the effect of other laws; and prohibitions on selling or renting information for mailing lists (PPSC, 1977b).
A decade later, the Computer Matching and Privacy Protection Act of 1988 (P.L. 100-503) amended the Privacy Act to include a new section of conditions that must be met before computer matching would be permitted. Another new section pertained to computer matching and required: (1) verification of adverse administrative actions and provision for individuals to contest findings and (2) notification of the public and evaluation of the effect of new systems or matching programs.
OPTIONS FOR PROTECTING PRIVACY AND CONFIDENTIALITY OF HEALTH-RELATED DATA IN HDOs
Two assumptions should drive the policymaking process with respect to privacy protection strategies and options for the establishment and operation of HDOs. First, from both a public policy and a legal standpoint, privacy protection will be a material issue. Accordingly, the issue warrants careful attention. Second, because HDOs are not health care providers or federal entities, HDOs will escape the reach of most existing privacy law. Nevertheless, many of the entities contributing data to HDOs will be bound by confidentiality obligations, and these obligations may affect their ability to submit person-identifiable data to HDOs, particularly if HDOs do not adopt stringent protective measures. That is, entities contributing information to HDOs will not escape existing privacy law.19
The committee's prevailing assumption is that HDO policymakers will be under pressure to develop effective privacy protection safeguards. They will also enjoy some degree of flexibility in the development and implementation of those safeguards and will have a striking opportunity to develop internal safeguards in advance of public or legislative pressure. The development of computerized databases can be seen as—or can evolve into—a way of giving people greater confidence about and real control over their personal information. When considering policies about privacy that might be implemented, Gostin (1993) posed seven questions about the human rights impact of disclosure of information that should be addressed even before data are collected.
- 1.
-
What is the purpose of the information?
- 2.
-
Will collection achieve a compelling public health purpose?
- 3.
-
Will collection result in effective health policy; that is, might it drive people underground if they fear the consequences of disclosure?
- 4.
-
Who will have access to the information? Can it be disclosed by force or law? What will be the effect of negligent disclosure?
- 5.
-
What impact will it have on human rights-is there a stigma to individuals or communities?
- 6.
-
Are there less invasive alternatives?
- 7.
-
What safeguards are available to reduce the risks?
The committee views these points as useful considerations for fashioning a sensible approach to privacy protections and choosing among a range of options for protecting privacy and confidentiality. Threats to confidentiality and privacy might be seen as posing options within a series of "layers" of protection. Such layers could include: (1) uniform state or federal preemptive legislation; (2) enabling legislation and organizational articles of incorporation and bylaws; (3) limiting categories of information acquired or accessed by HDOs; (4) administrative rules and regulations including institutional and user codes of conduct and employee training; (5) comprehensive security safeguards in all automated systems and networks; (6) controlled access to databases; (7) techniques to reduce the risk of inferential identification, such as suppression of small cell sizes; and (8) enforceable administrative, civil, and criminal sanctions and penalties for misuse. At each level, more stringent efforts at security incur trade-offs of inconvenience for users and costs born by the parties-patients, users, supporting organizations, providers, researchers, and (perhaps) taxpayers.
In the remainder of this section, several options for addressing privacy protections are presented. The committee's recommendations—in effect, judgments about the seven questions posed by Gostin and choices among a set of options—appear in the next section of this chapter. They address uniform legislation establishing a clear set of rights, duties, administrative procedures, and remedies for all persons and institutions affected by the implementation and operation of HDOs. The recommendations also address administrative policies and procedures that HDOs should adopt.
Uniform Legislation
Federal Preemptive Legislation
The committee considered one important option to be enactment of federal preemptive legislation. Federal preemptive legislation refers to federal law that supersedes any state law or legislation that either covers the same matter or conflicts with the federal legislation. Such preemptive legislation in this area could establish uniform requirements for the preservation of confidentiality and protection of privacy rights for health data about individuals because health data, particularly in electronic form, will cross state boundaries when accessed and disclosed by HDOs.
As noted earlier, existing state laws pertaining to the actions of recordholders will likely not apply to HDOs, but HDOs might wish to comply with them. Yet, state protections for confidentiality of data contributed to HDOs may be lacking, inconsistent, or even in conflict from state to state. Where they exist, they create an extraordinary patchwork of regulations embedded in laws pertaining to a variety of recordkeepers such as hospitals, HMOs, nursing homes, state health departments, insurers, employers, and so forth. A brief review of state statutes indicated that in one state more than 50 different statutes and regulations pertain to the confidentiality of medical information. Compiling, understanding, and complying with conflicting or arcane regulations for each state would be virtually impossible for HDOs operating in numerous states. Making such policies clear to the public would likely be even more hopeless.
During the period of this study, a number of groups were examining the questions of privacy rights with electronic transfer of health information. Among the more significant was the Workgroup on Electronic Data Interchange (WEDI).
In its 1992 report, WEDI identified three principles for databases containing sensitive personal information that could be associated with identifiable persons; these principles involved computer system security, fair information practices, and privacy protection. To satisfy these principles, WEDI recommended federal preemptive legislation. Its proposals referring to the collection, storage, handling, and transmission of data were intended to facilitate and ensure the uniform, confidential treatment of person-identifiable information in electronic environments.
WEDI recommended that federal legislation include the following steps and provisions:
-
establish uniform requirements for preservation of confidentiality and privacy rights in electronic health care claims processing and payment;
-
apply these requirements to the collection, storage, handling, and transmission of individually identifiable health care data, including initial and subsequent disclosures in electronic transactions by all public and private payers, providers of health care, and all other entities involved in the transactions;
-
exempt state public reporting laws;
-
delineate protocols for secure electronic storage and transmission of health care data;
-
specify fair information practices that ensure a proper balance between required disclosures, use of data, and patient privacy;
-
require publication of the existence of health care data banks;
-
establish appropriate protections for highly sensitive data, such as data concerning mental health, substance abuse, and communicable and genetic diseases;
-
encourage use of alternative dispute resolution mechanisms where appropriate;
-
establish that compliance with the act's requirements would be a defense to legal actions based on charges of improper disclosure;
-
impose penalties for violations of the act, including civil damages, equitable remedies, and attorneys' fees where appropriate; and
-
provide for enforcement by government officials and private, aggrieved parties.
As described earlier in this chapter, protections for data independent of the recordholder is an important option to consider, and federal legislation provides an opportunity to establish such protections.
Privacy advocates see two possible drawbacks to federal legislation. First, such legislation could weaken rather than strengthen protections if the federal legislation is less stringent than good state legislation—hence the need for strong federal law. If federal legislation leaves room for states to implement more stringent standards, multistate HDOs will still, however, be subject to conflicting requirements, and this may add to, rather than decrease, administrative cost and complexity.
Second, to the extent that federal legislation encourages uniform standards that foster interlinkage and creation of a national database, it will contribute to the development of national databases and, by linkage, to non-health-related databases, dossiers, and national identification systems. The committee's dim view of the development of national identification systems has already been noted.
Uniform State Legislation
The main alternatives to federal legislation would be the status quo or enactment of model state acts. Adoption of uniform state legislation would undoubtedly involve a lengthy and cumbersome process and would not ensure adoption by all states. Even if a uniform law were adopted by all the states, it would likely be adopted with variations by some states, much as in the case of the Uniform Commercial Code. Hence, the committee was not sanguine about the utility of this approach.
Options for Consent and Participation Rights
The discussion above related mainly to federal preemptive legislation. Whether or not such legislation is adopted, HDOs will need internal policies, although such organizational, administrative, and governance approaches would be informed by existing (if not new) federal or state law.
Consent and participation rights for record subjects are essential elements of the Privacy Act. They provide individuals with rights to see, copy, and correct their records, as well as grant limited rights to authorize the collection and disclosure of information. State statutes routinely give persons a right of access to data about themselves and a role in authorizing (or limiting) third-party disclosures. HDO designers will be able to select from a range of consent and participation options that run from weak to quite stringent, with middle-range strategies possibly a useful approach.
HDO Access to Data
Notification. At a minimum, HDOs could publish or give record subjects notice that information about them—including information that the individuals provide directly to participating health care providers, insurers, and employers—will be accessible by the HDO. They might also require notification by entities submitting data to HDOs. Presumably this notice would provide individuals with at least a cursory description of the manner in which HDOs or their agents might use their data.20 They would have no further rights, however, in terms of access to the data. Under current law in many states, patient consent will be required to transmit data to or allow access by the HDO (see footnote 18).
General releases. HDOs could be designed so that individuals would simply be notified about their data being accessible to HDOs, but would also sign a general release authorizing participating providers, payers, and employers to share personal data with HDOs. The presumption, of course, is that such a release (and its implications) is well understood by those signing it. Such a general release might also be crafted to give the HDO a blanket authorization to redisclose.
From a legal standpoint, this approach, however modest it may seem, would be adequate except in the case of extremely sensitive health information such as alcohol and drug abuse, mental health treatment, and AIDS information. Extremely sensitive health record data (e.g., that just noted) generally could not be shared with the HDOs or redisclosed by the HDOs pursuant to general release under existing federal and state law.
Another option is for individuals to receive a complete and detailed written description of an HDO's permissible disclosures and other information practices and a complete description of their information rights.
Stronger options would allow individuals the right to revoke their authorization and, in any event, the authorization would be effective only for a limited period. Even stronger options would require that individuals sign a specific consent form (described below) each time they provided data accessible to an HDO or to HDO participants. In this case, each data element might require separate authorization and expiration dates.
Other Consent and Participation Rights
Even if this approach were to meet minimum legal requirements, however, it is likely to be politically unacceptable for issues of database maintenance and disclosure by the HDO. Given the comprehensiveness and sensitivity of HDO databases and the high level of public concern about privacy, the committee expects that privacy advocacy groups, legislators, the media, and other public opinion leaders will insist that HDOs be brigaded with substantial consent and participation rights.
Participation. An HDO offering participation rights at the high end of the ''protection spectrum" would have all or most of the following characteristics:
-
Individuals would receive a complete and detailed written description of an HDO's permissible disclosures and other information practices and a complete description of their information rights.
-
Record subjects would have a right of access to all data about themselves that are held in the HDO at a nominal charge. Access rights would include the right to receive a copy of their records, not merely a right to review their record.
-
Persons would have a right to correct and amend their records and to add a rebuttal statement if the HDO refused to make a requested correction or amendment.
-
Record subjects would have a right to inspect an "audit trail" that can identify all uses, disclosures, and other access events involving their own files.
-
Alternatively, record subjects would receive notice in the mail each time the HDO discloses their data to third parties or, at the least, each time HDO data are used to make an adverse decision affecting the individual. This latter formulation is not dissimilar to current notice requirements in FCRA.
Disclosure Options
Rules about disclosure and confidentiality are at the heart of any information privacy policy. Here HDOs will enjoy a significant degree of legal flexibility. Under existing law, HDOs could adopt confidentiality policies that span a spectrum from a disclosure-oriented policy at one end to a strict confidentiality policy at the other. From a political standpoint, however, HDO proponents are likely to see advantages in opting for a confidentiality-sensitive policy for person-identifiable data.
Disclosure-Oriented Options (Weak Options)
Under a disclosure-oriented policy, all person-identified or person-identifiable data accessible to HDOs would be available to participating parties for any purpose and without specific subject authorization. Exceptions would apply to particularly sensitive kinds of data, such as records on substance abuse, AIDS, and genetic tests. Even under existing law most of these records cannot be made available without specific authorization. Adopting a disclosure-oriented approach would also make most person-identifiable information available to third parties, as long as the user had a legitimate business purpose for accessing the information.
Furthermore, under a disclosure-oriented policy HDOs would routinely make person-identifiable information available in response to subpoenas, other forms of compulsory process, or formal, voluntary requests from law enforcement or regulatory authorities. If a disclosure-oriented policy were adopted, the principal confidentiality restrictions would relate to the handling of sensitive subsets of health record information and to wholesale disclosures of identifiable information to the general public. The committee rejected this broad disclosure-oriented option as incompatible with its values and the effective implementation of HDOs.
Confidentiality-Oriented Options (Strong Options)
In contrast, a confidentiality-sensitive approach to disclosure would include some, if not all, of the elements listed below.21
-
HDOs could release information only in non-person-identifiable formats except under very restricted circumstances.
-
HDOs could not release any information in personally identifiable form from an HDO database to third parties without a specific authorization, either signed or given electronically by the person in question.
-
HDOs could opt never to release person-identifiable information even with subject consent, or to release information in a customized format that blocked parts of a subject's record, depending upon the user and use for which it was requested.22
-
HDOs could refuse to provide person-identifiable information to third parties that intended or could use the information to make decisions about an individual's access to particular benefits (standard processing of health insurance claims would be an exception to this policy).
-
HDOs could require users to sign "confidentiality agreements." These agreements would obligate users to safeguard information obtained from the HDO and use it only for the purpose for which it was provided. Violations of the agreement would give the HDO (and perhaps record subjects) a claim of either breach of contract or of confidentiality (or both) against the offending user.
-
They would adopt a policy of refusing to comply with voluntary requests for access from law enforcement or regulatory agencies.
-
In legal matters, HDOs could resist compliance with subpoenas or other forms of compulsory process, assert all available privileges, and notify record subjects of an access request so that they could contest production. (The Uniform Act noted earlier takes a similar approach with respect to compulsory process.)
Governance Options as an Approach to Privacy Protections
Issues relating to the structure and governance of an HDO will be critical to both the substance and the appearance of privacy protection and, therefore, to the HDO's political acceptability. In this context, the principal question will be the extent of government involvement in the operation of the HDOs. In the absence of federal preemptive legislation, state legislation might include a number of options. Although the laws in this section are all state oriented, if federal preemptive legislation is enacted, it would set confidentiality standards for HDOs and possibly preempt state statutes.
State-Based Systems
At one end of the governance spectrum, HDOs could be operated by state or local (but not federal) agencies. This kind of structure has privacy benefits. Constitutional privacy protections, for example, would attach if the HDOs were operated by public agencies. Further, governmental operation would increase the likelihood of effective public and regulatory oversight and accountability. Under this formulation, legislative hearings for budgetary and policy purposes could be expected to be a regular feature of the HDO process.
State or local agency operation of an HDO also carries significant dangers to privacy. This level of government involvement would exacerbate concerns about the linkage of HDOs with other sensitive government databases and the creation of a dossier system. Pressure for public access to HDO health record data means that HDOs will need to be exempted from state FOI laws.
Were an HDO to be operated by a state agency, it would resemble in several ways health data commissions now in place in a number of states. Because some of these have operated for some time, typical characteristics are worth reviewing here.
Iowa, for example, created a health data commission as a "statewide health data clearinghouse for the acquisition, compilation, correlation, and dissemination of data from health care providers, the state Medicaid program, third-party payers, and other appropriate sources." The Iowa statute gave the commission authority to require providers, payers, and others to submit medical record information in a person-identifiable format to the commission. It also provided that medical record data furnished to the commission would not constitute a public record and that all of the confidentiality protections available under the laws of Iowa would apply. Data releases suppress patient identifiers and suppress data in small cells. Early in 1993, bills introduced in the Iowa Senate and House called for implementation of a community health management information system (CHMIS) by the Health Policy Corporation of Iowa through its subsidiary, the Health Information Management Center. The main elements of CHMIS entities were given in Chapter 2.
Private-Sector Systems
At the other end of the governance spectrum, HDOs could be operated by purely private, for-profit or not-for-profit entities with no governmental status or legislative charter. Even in this posture, an HDO could take steps in structure and governance to maximize privacy protections. These steps could include:
-
establishing a privacy ombudsman to respond to patient problems or complaints;
-
establishing an advisory committee of representatives of organizations affected by the HDOs, including consumer, patient, and privacy advocacy groups;
-
adopting a comprehensive privacy code to regulate all aspects of the collection, maintenance, use, and dissemination of person-identifiable data;
-
designating a high-level employee to assure compliance with applicable privacy policies and standards and to prepare an annual "privacy status and compliance report" for submission to the boards of directors or advisory committees of HDOs;
-
initiating a program of periodic audits to gauge compliance with privacy standards and a privacy impact audit of all new programs or functions; and
-
creating an employee privacy training program.
Mixed Governance Systems
For privacy, an attractive governance approach is a middle ground, wherein the entity operating the HDO would be a private, not-for-profit organization with a legislative charter. Such an approach is under way in Washington State. A legislative charter could serve at least nine purposes in the protection of privacy.
First, a legislative charter could bring constitutional privacy protections to bear in some circumstances. Second, it could spell out a statutory cause of action for record subjects, which included remedies such as attorneys' fees and liquidated damages. Third, it could give statutory effect to the HDOs' confidentiality and other privacy standards. Fourth, a legislative charter would affect how federal law characterizes HDOs and help to dispel any confusion about the legal status of an HDO (by stating that the entity is not a health care provider, a payer, or a consumer reporting agency). Fifth, it could establish a "shield" to immunize the HDO databases from discovery and other forms of compulsory process in state courts and administrative proceedings. Sixth, it could criminalize egregious information practices such as intentional breaches of security or willful, unauthorized releases of information. Seventh, such a statute could charge the attorney general or some other appropriate state agency or official with oversight and enforcement responsibilities. Eighth, the statutory charter could institutionalize privacy safeguards such as auditing and training. Finally, it could require an annual report to a legislative committee detailing the HDO's compliance with privacy safeguards or otherwise establish an effective oversight mechanism for assisting the HDO in complying with privacy safeguards.
State charter and mixed governance options will continue to be hampered by the possibility that HDOs will operate in multistate areas. In the absence of federal legislation, this lack of uniformity of requirements or predictability of legal consequences of system design and operational characteristics would be major problems.
Other Administrative Options to Protect Privacy and Confidentiality
Security risks may be exacerbated for HDOs that have large numbers of remote on-line terminals. HDOs will need to implement comprehensive, state-of-the-art administrative, personnel, physical, and technological security safeguards; of special interest are employment agreements and security systems design. Whatever confidentiality policies HDOs adopt or are imposed by law, HDOs must be able to implement them and assure their effectiveness.
Employee agreements would, at a minimum, require employees to observe guidelines related to hard-copy reports, diskettes, and downloaded data and would instruct them about the dangers of altering, destroying, or revealing data and the penalties attached to infractions. For employees such steps include: requesting only reports needed for a given job; notifying a security administrator of changes in duties; safeguarding confidential materials; sharing information only with authorized users; using only approved user codes and passwords when requesting system access; not sharing such codes and passwords with anyone, employee or not; disposing of reports and materials in a secure manner; logging off and securing equipment when leaving a terminal; and reporting data and system misuse.
Features to limit insider and outsider threats include providing systems to conduct audit trails, having full-time security officers to enforce overall policy and monitor the system, employing expert systems to note unusual patterns of requests or employee behavior, assigning personal identification numbers (PINs) and passwords, and granting access to parts of records only on a need-to-know basis.
One option among many for addressing some of these problems is encryption (see OTA, 1993); in this process data are electronically coded so that only the dataholder and authorized users can decode the data. Medical records may require secured—that is, encrypted—communication because the inherent value of the records is very high.
Another option is the creation of a data integrity board. The Computer Matching and Privacy Protection Act of 1988 (P.L. 100-503) specified the creation of data integrity boards for federal agencies to oversee the implementation of computer matching programs. These boards were charged with overseeing a number of administrative requirements, which include the following: to issue annual reports on matching activities and any violations that have occurred; to serve as a clearinghouse for receiving and providing information on the accuracy, completeness, and reliability of records; to provide interpretations and guidance on requirements; and to review agency recordkeeping and disposal policies. These tasks illustrate what HDOs will need to oversee in their own operations.
COMMITTEE RECOMMENDATIONS
Overview and General Principles
In arriving at its set of recommendations concerning privacy and confidentiality protections, the committee reviewed federal and state statutes and regulations and common law that might apply to HDOs; it also took under advisement parallel studies related to these topics at the IOM and elsewhere. The committee ultimately arrived at a set of preferences among the various options described above, presented in the form of recommendations.
If HDOs are government entities or established by legislative charter, patients' rights embodied in federal, state, and local laws and statutes may apply to the acquisition and disclosure of person-identifiable data. Given: (1) the unprecedented comprehensiveness and inclusiveness of information in the files held by HDOs (as those terms were used in Chapter 2), (2) the generally scanty and inconsistent legal protections across geopolitical jurisdictions, and (3) the current public interest in and concern about privacy protections, the committee believes that HDOs have both an obligation and an opportunity to fashion well-delineated privacy protection programs that will, at the same time, foster the realization of HDO goals. Some of these protections, such as the establishment of data protection boards and organizational policies regarding security and access control, can be implemented in the short term. Others, such as passage of federal preemptive legislation, will likely require longer-term efforts.
Preemptive Legislation
RECOMMENDATION 4.1 PREEMPTIVE LEGISLATION
The committee recommends that the U.S. Congress move to enact preemptive legislation that will:
-
establish a uniform requirement for the assurance of confidentiality and protection of privacy rights for person-identifiable health data and specify a Code of Fair Health Information Practices that ensures a proper balance among required disclosures, use of data, and patient privacy;
-
impose penalties for violations of the act, including civil damages, equitable remedies, and attorney's fees where appropriate;
-
provide for enforcement by the government and permit private aggrieved parties to sue;
-
establish that compliance with the act's requirements would be a defense to legal actions based on charges of improper disclosure; and
-
exempt health database organizations from public health reporting laws and compulsory process with respect to person-identifiable health data except for compulsory process initiated by record subjects.
The committee believes that both processes in the last item—public health reporting and responding to compulsory process such as subpoenas—should remain the continuing responsibility of the provider, as is now the case.
Arguments for Federal Legislation
The committee concludes that federal preemptive legislation is required to establish uniform requirements for the preservation of confidentiality and protection of privacy rights for health data about individuals because health data, particularly in electronic form, will cross state boundaries when accessed and disclosed by an HDO. In general, the committee subscribes to the positions laid out in the WEDI report (1992) and thus advocates federal preemptive legislation in preference to model state legislation or similar nonfederal approaches. It further advises that Congress enact such legislation as soon as possible. At a minimum, federal legislation should establish a floor and allow states or HDOs to implement more stringent standards so that it does not weaken state-imposed safeguards.
Attaching Privacy Protection to Data
Although current state protections often apply duties of confidentiality to the recordkeeper (e.g., the hospital), this protection is no longer in effect once the data have left the recordkeeper's control. This means that health data can be deprived of legal protection unless such protection is specified by another law; furthermore, such protection is likely to be left to the discretion of the organizations or individuals who acquire such information as secondary data. At the present time, that is little shelter indeed.
Therefore, legislation should clearly establish that the confidentiality of person-identifiable data is an attribute afforded to the data elements themselves, regardless of who holds the data. There is precedent for attaching umbrella protection to sensitive data either by regulation or by law. Examples include Executive Order 12356 (April 12, 1982), which gives defense agencies authority to establish levels of sensitivity and classify information in them; the Tax Reform Act of 1976 (P.L. 94-455), which stipulates that tax information is considered confidential, requires that the IRS and states protect it as such. According confidentiality protections to data, not to holders, would help to remedy the current lack of protections and to simplify the establishment of, compliance with, and communication of health information practices.
Uniform Requirements
The committee has concluded that ensuring an appropriate balance between the protection of confidentiality of health data about individuals and disclosures of database information requires several important features in legislation or implementing regulations. The first is the inclusion and observance of selected fair information practices, such as those found in the Privacy Act of 1974.23 These practices—not yet available or understood in the health sector—are described in more detail in the following recommendation on data protection boards. Their significance lies (apart from historical precedent) in promulgating uniform expectations and protections for health data.
Second, federal legislation can be expected to encourage standard setting (e.g., connectivity and transmissions standards). As noted in Chapter 2, the lack of standard setting is a major obstacle to the development of automated medical records (GAO, 1991, 1993a); it will be no less a problem for advanced HDOs. Thus, the committee sees federal legislation as one more mechanism for addressing this problem for all computer-based systems dealing with health data.
Specific Elements of Federal Legislation
Good information practices24 include the collection, transmission, and storage of only the information that is needed. They imply (if not explicitly demand) that data not be collected for unlawful purposes. Thus, proper preemptive legislation should also provide for enforcement by government officials and private aggrieved parties and should impose penalties for violations of the legislation. These might include civil damages, equitable remedies, and attorney's fees where appropriate. It will be important that the legislation clarify whether individuals have standing to bring suit.
HDOs may find themselves in complex legal thickets as demands mount for disclosure of various types of information, some of which may well include protected person-identifiable data. If it is likely that such disclosure will be deemed improper, HDOs may be understandably unwilling to release or disclose much information. This stance may in turn stifle the very contributions that HDOs can offer (as discussed in Chapters 2 and 3). To overcome this possible aversion to risk on the part of HDOs, the committee argues that compliance with requirements of any federal legislation in this area ought to be a straightforward and sufficient defense against legal actions based on charges of improper disclosure. In taking this position, however, the committee further stipulates its expectations that federal legislation will have strong privacy and confidentiality protections that meet, if not exceed, the usual provisions of fair information practices statutes or regulations.
Exemption from Compulsory Reporting and Compulsory Process
A special aspect of the committee recommendation concerns federal, state, and local public health reporting laws and compulsory process. Federal legislation should exempt HDOs from these types of requirements on the grounds that the primary dataholders or originators are the proper target for such laws and regulations. The issue may be especially acute where state laws specify reporting by providers or by "anyone who has knowledge of certain events" (e.g., a reportable communicable disease, a gunshot wound, or child abuse). The committee believes that HDOs ought not to be considered, for these purposes, either a provider or an "anyone" with knowledge of reportable events. To make this clear, the committee believes that HDOs should be directly exempted from such reporting requirements. It should be noted, however, that electronic transfer of such data from health providers to an HDO or its databases would facilitate independent reporting to the appropriate health agency by the provider and thus improve the completeness of those agencies' records.
In much the same way, the committee agrees that data that are essential for conduct of authorized activities by, for instance, the Internal Revenue Service, the Federal Bureau of Investigation, or legal authorities through subpoena or court order should be obtained from the primary recordholder, not the HDO. The committee believes that exemptions from compulsory reporting and compulsory process regarding third-party disputes will strengthen the claims regarding, and the actual protections accorded, the confidential person-identifiable health data held by HDOs. Compulsory process should apply, however, in disputes between HDOs and record subjects.
If federal (or state) legislation does not grant such exemptions to HDOs, then the committee's view is that HDOs should adopt a policy of refusing to comply with requests for access from law enforcement or regulatory agencies to the extent permitted by law, and it should actively seek exemptions in future federal and state legislation. They should also adopt policies of resisting compliance with subpoenas or other forms of compulsory process, asserting all available privileges, and notifying record subjects of an access request so that subjects would have an opportunity to contest production of such data.
Data Protection Units
HDOs will need clear, enforceable, written organizational policies and procedures in several areas: patients' rights regarding their own data; how to protect medical information and materials; how to ensure the accuracy of data; and how to know they have gained compliance with their policies. Members of the public should be able to request and receive clearly written materials describing these policies. Although precise policies cannot be written to cover every eventuality, they must be broad enough to address the most common situations, such as types of data, and potential requestors.
If an HDO is chartered by legislation, legislative language will undoubtedly describe its goals. HDO policies implementing these goals, however, must emanate from the top leadership of the organization. Leadership must delineate an ''enforceable expectation of confidentiality" (as advocated by the PPSC, 1977a) and make clear that breaches will be rigorously addressed. Organizations should also make considerable efforts to educate (and reeducate) staff and the public (i.e., potential requestors) about these policies.
RECOMMENDATION 4.2 DATA PROTECTION UNITS
The committee recommends that health database organizations establish a responsible administrative unit or board to promulgate and implement information policies concerning the acquisition and dissemination of information and establish whatever administrative mechanism is required to implement these policies. Such an administrative unit or board should:
-
promulgate and implement policies concerning data protection and analyses based on such data;
-
develop and implement policies that protect the confidentiality of all person-identifiable information, consistent with other policies of the organization and relevant state and federal law;
-
develop and disseminate educational materials for the general public that will describe in understandable terms the analyses and their interpretation of the rights and responsibilities of individuals and the protections accorded their data by the organization;
-
develop and implement security practices in the manual and automated data processing and storage systems of the organization; and
-
develop and implement a comprehensive employee training program that includes instruction concerning the protection of person-identifiable data.
Establishing a Data Protection Board
The commitment of the governing body and executives of the HDO to protection of confidentiality will be critical, and these objectives should be written at the outset into the organization's bylaws. One useful mechanism for accomplishing these goals is to establish a policy and oversight "data protection" and "data integrity" unit or units to promulgate, publicize, oversee, and enforce formal policies and procedures concerning access to and release of data. Such an entity within an HDO might be known generically as a data protection board, and that is the term employed in this report.25 (Implementation of such policies and procedures would be the responsibility of specific operational arms of the organization, not the policy units themselves.) Such policy boards and their formal policy statements should be in place before HDOs begin operations, and regardless of whether such policies are specified and enacted in federal preemptive legislation. Policies and procedures should explicitly deal with authorized and unauthorized access to and authorized and unauthorized release of information from HDO databases.
Functions and responsibilities. A data protection board would have full authority to monitor data protection activities, intervene in potentially harmful situations, make exceptions to privacy and confidentiality policies on a case-by-case basis, address questions of new uses and new users of information over time, and undertake other responsibilities that will fulfill the spirit and the letter of the organization's policies.
In terms of actions that HDO data protection boards might undertake, they should: (1) promulgate a code of fair health information practices (or implement one if included in federal or state legislation) and make that code available on request to any member of the public; (2) monitor compliance with such a code, audit for breaches of confidentiality, and respond in a timely way to public concerns; (3) establish, publicize, and implement formal policies and procedures concerning access to and release of data before full operation of their databases begins; and (4) ensure that such policies and procedures deal explicitly with authorized and unauthorized access to and authorized and unauthorized release of information from the database.
Drawbacks and limitations. The committee acknowledges that data protection boards will not provide a full solution without external (and probably federal) legislation and commitment from the governing boards and top leadership of HDOs. Moreover, this stance raises the issue of whether a data protection board should be a function of an HDO—which may be private, quasi-public, or public—or a governmental function applicable to all HDOs. Because of the limited powers of an HDO, particularly if it is private or quasi-public, the data protection board will be able to enforce its policies rigorously only within the organization; externally it can merely track the compliance of others that have contractual obligations to the HDO, but it will not have jurisdiction over them. In the absence of a law giving it added powers, the most that such a board could do about breaches of confidentiality by a party that received information would be to pursue legal remedies for breach of contract or any violation that may have occurred.
An additional problem with relying solely on contractual protections is that the real harm from improper disclosure of information will be suffered not by the HDO, but by persons who in all likelihood will not be a party to the contract with the HDO. (The exception might be when all such contracts name as third-party beneficiaries individuals whose information is on the system, but the committee regarded this as a remote possibility.) In the absence of legal action by such third-party beneficiaries, the liability for improper redisclosure may be minimal.
Developing Administrative Policies and Procedures
General administrative points. HDOs should develop and promulgate strong internal policies and procedures concerning the protection of health information with policies on public disclosure of information and evaluation studies. The committee further advises that such policies, which it assumes will be set by the data protection boards, specifically address the following administrative points:
-
who in the organization has final responsibility for setting, monitoring, and enforcing policies and procedures;
-
who inside the organization is authorized to have access to which data, and under what circumstances;
-
who has authority to override policies (i.e., what are the unusual circumstances, to be decided on case-by-case basis, and who will make these decisions); and
-
what are the penalties for unauthorized access or disclosure of protected information, and whether they will differ if disclosure is inadvertent, undertaken for financial gain, or for other inadmissible purposes.26
Implementation of such policies would likely be spread throughout the operating organization. For example, the electronic data processing department would be responsible for implementing security procedures, and the personnel department would likely carry out employee training in appropriate conduct. Some blend of oversight and operational officers would determine authorized uses of the data and rule on the exceptional case.
Policies should cover topics such as types and sources of data over time, notice to individuals about the databases accessed by the HDO, and similar matters. As a broad principle, the committee believes that HDOs must draw on the Privacy Act of 1974 and its principles of Fair Information Practices. This code and other significant issues that HDOs should address are discussed below.
Fair Health Information Practices. The committee strongly advises that HDOs include in their policies and procedures fair health information practices such as those provided for in the Privacy Act; it further urges that HDOs consider applicable revisions of the Privacy Act suggested by the PPSC and others. Any HDO should consider this code as the foundation of its privacy framework and depart from it only after careful consideration and explanation. There will be a direct relationship between, on the one hand, the extent to which record subjects are assured of notice, access, consent, and other rights with respect to information maintained in an HDO and, on the other hand, the political acceptability of HDOs as a concept or a reality in a given location. The committee thus sees such fair health information practices as critical elements in the eventual success of HDOs.
One procedural element of fair information practices is notice to subjects of their inclusion in a database. HDOs might provide for public notification in a variety of ways. At a minimum, periodic published notices in newspapers or public interest broadcast spots could alert individuals, indicate how more information could be obtained, and serve a public education function in explaining what HDOs do. Notice might also be given at the time a health service is provided or when enrolling in a health insurance or provider plan; a case in point is when authorization to access the HDO is given.
Types and sources of data. The committee believes that HDOs should collect only personal information that is necessary to achieve their publicly stated purposes and that they should identify, in writing, specific categories of personal information that they will not obtain under any circumstances. Information relating to an individual's exercise of First Amendment rights might be an example.
HDOs should agree to collect personal information to the fullest extent possible directly from record subjects and their health care providers. This stance reflects the approaches of both the Privacy Act and the PPSC.
Management of records over the long term. Databases cannot be permitted to grow without bounds. Given that the committee cannot foresee how the HDOs will function, it cannot be more specific than to urge that HDOs adopt policies and procedures for archiving records. HDO data protection boards will need policies to respond to an individual's request to purge or seal a record.27
Confidentiality agreements. HDOs should require those who are given access to HDO data to sign confidentiality agreements. These legal agreements would obligate users to safeguard information obtained from HDOs and use the information only for the purpose(s) for which it was provided. Violations of the agreement would give the HDO (and perhaps record subjects) a breach of contract and confidentiality claim against the offending user.
The effort to require recipients to protect confidentiality brings one squarely up against the limitations of contract provisions in this area. Without preemptive federal legislation that requires data recipients to protect the data they obtain in the same way that the HDOs are required to protect those data, no protection can be assured. First, HDOs would have to police the uses made of data by all recipients, and they would have to police redisclosures. As a practical matter, these steps are impossible. Second, no mechanism such as a notarized affidavit would suffice, because such an instrument is merely a sworn statement and has no special status as a contract. A representation of intended use in a confidentiality agreement should be sufficient as a contract. In short, contractual protections are weak, so they should be used only as an adjunct to, and not as a substitute for, appropriate new federal legislation to protect the confidentiality of sensitive patient information held by HDOs.
Routine blocking of sensitive data. Legislation and organizational policies have sometimes distinguished among levels of sensitivity of various elements of health-related data in the belief that it is possible to identify categories of data that warrant special protection (IOM, 1991a; WEDI, 1992). For instance, laws protect data related to treatment in federal drug abuse treatment facilities that receive federal funds.
Despite precedent for adopting such a stance, this committee has decided otherwise. It has concluded that a given data element cannot always be reliably designated as inherently sensitive; rather, the sensitivity of data depends on the kinds of harm to which individuals are or believe themselves to be vulnerable if the information were known to others. Such assessments could differ dramatically from one person to another, one circumstance to another, one place to another, and over time as cultural attitudes change. Rather than recommending special protections for certain categories of data, the committee prefers that all data accessed by HDOs be afforded stringent, and essentially equal, protection.
Blocking divulgence by individuals of sensitive data. If no data are routinely to be considered "sensitive" and thus more stringently protected than other types of data, then might it be reasonable to permit individuals to block divulgence of particular kinds of information? That is, should persons be able to flag or label certain data as special or sensitive, so that those particular facts, specific to those individuals, would not be divulged to anyone? This could be accomplished either by: (1) permitting individuals to block information from disclosure without flagging that information as being so blocked or (2) by letting them block the information but labeling it as blocked. The committee concluded that neither of these options, although perhaps attractive from the point of view of autonomy and empowerment, was desirable as a means of protecting privacy.
The main reason for this position is that, unless care is taken in designing the system, flagging information as having been blocked might in some circumstance defeat or even exacerbate the challenge to privacy; such a label or flag would alert anyone reviewing the material that it includes sensitive data. More insidious from the viewpoint of a treating physician— for whom this information may someday be a proxy medical record (as when information is unavailable by some other means)—it would compromise his or her ability to care for the patient. Furthermore, if blocked material is not so flagged or labeled, the consequences for treating physicians could be even more disastrous if that blocked information (e.g., the existence of a serious chronic condition or use of a particular medication) is directly relevant to clinical decisions. Although it is true that patients can always omit information in a face-to-face encounter, it would seem to defeat one of the purposes of a database to allow it to be intentionally incomplete. Thus, the committee does not subscribe to the view that specified material could be blocked (masked), whether labeled that way or not.
Overseeing Data Integrity
HDO data protection boards would oversee safeguards to prevent health information from being disclosed to unauthorized recipients. They may also need to be responsible for oversight of the protection of data from unauthorized alteration and for data accuracy and completeness. (These tasks might, alternatively, be assigned to a "data integrity" unit, board, or committee.)
At a minimum, this board would need to ensure that data and programs are changed only in a specified and authorized manner, and it would be responsible for assessing and reporting the accuracy of the HDO's data. Data integrity may be maintained by implementing security measures, by implementing procedural controls, by assigning responsibility, and by establishing audit trails as described earlier in this chapter.
Security requires proper system design driven by policies that have been determined and approved by the governing board, chiefly because software and hardware vendors are likely to implement only the level of security specified by the HDOs. Access must be limited to authorized users. Mechanisms and procedures must also be developed and implemented before the network becomes operational. These should address how data integrity will be maintained by preventing alteration or loss of data and what steps will be taken for authenticating users and maintaining records of communications with users. Procedures to ensure availability and recovery after unanticipated disruptions (e.g., power loss, fire) are also crucial, including assurance that the systems resume operation in a secure state and that data integrity is guaranteed.
Security in these environments presents special challenges, in part because it is only as adequate as that provided for the least secure database on the network. Further, remote access to computer systems, the possibility of accessing information over public telecommunications systems, and advances in standardization of data elements and transmission requirements will enhance the opportunities for data linkage, but they will also magnify the need for security protections. Data networks will become increasingly attractive to sabotage and access for financial gain and thus require special attention to manage these risks.
The basic intent is to provide assurance that the system, its resources, and information are protected against harm and that the information and resources are properly accessed and used by authorized users. The board should ensure that, at a minimum, the following list of security safeguards would be in place internally for a defined operational system and environment:
-
a defined set of users;
-
prescribed data and operational programs;
-
defined network connections and interactions with other systems; and
-
protection against defined threats against the system, its resources, and its data.
Safeguards might include policy guidance in several areas: procedures for granting access to systems and assigning passwords; administration and training of security officers for conduct of audits and disaster preparedness; and oversight of management review of safeguards and inspections.28
HDOs' resources will probably never be sufficient for all the activities and responsibilities envisioned for them. Long-term success is likely to be predicated in part on their ability to protect confidentiality of personal health data, and the committee believes that they will therefore have to devote adequate resources to some form of data protection board. It may well be that monetary or human resources sufficient to maintain independent data protection and data integrity units will not be available; those resource allocation decisions, however, are best left to individual HDOs.
Release of Person-identified Data
Policies Relating to Access and Disclosure
It is clear that the question of who outside the HDO has access to which data, under what circumstances, is supremely important; this is directly related to questions of disclosure and is the essence of the privacy issue from the patient's point of view. The committee takes up these matters in a series of recommendations (presented below) that refer to person-identified or person-identifiable information only. As laid out in Chapter 3, this committee recommends release and disclosure of information that protects patient identity but provides reliable, valid, timely, and useful descriptive and evaluative information on a full range of health care providers and clinicians. It also acknowledges that some HDOs will have claims processing and payment functions that will require transmittal of person-identified claims information between the provider and payer.
RECOMMENDATION 4.3 RELEASE OF PERSON-IDENTIFIED DATA
The committee recognizes that there must be release of patient-identified data related to the processing of health insurance claims. The committee recommends, however, that a health database organization not release person-identifiable information in any other circumstances except the following:
-
to other HDOs whose missions are compatible with and whose confidentiality and security protections are at least as stringent as their own;
-
to individuals for information about themselves;
-
to parents for information about a minor child except when such release is prohibited by law;
-
to legal representatives of incompetent patients for information about the patient;
-
to researchers with approval from their institution's properly constituted Institutional Review Board;
-
to licensed practitioners with a need to know when treating patients in life-threatening situations who are unable to consent at the time care is rendered; and
-
to licensed practitioners when treating patients in all other (non-life-threatening) situations, but only with the informed consent of the patient.
Otherwise, the committee recommends that health database organizations not authorize access to, or release of, information on individuals with or without informed consent.
Consent
In the last item, the committee has specifically recommended that consent for access to the database be a necessary and sufficient condition in only one circumstance: when needed by the treating practitioner. In such a situation it will be important that specific consent techniques be in place. The following requirements, similar to those in the Uniform Health Care Information Act, are based on PPSC recommendations for medical record information consent forms. Patient consent must:
-
be in writing or electronically provided in an acceptable manner;
-
be signed or authorized electronically by the individual on a date specified;
-
be clear about the entities being authorized to disclose information;
-
be specific about the nature of the information to be disclosed;
-
be specific as to the institutions or persons to whom the information may be disclosed;
-
be specific about the purposes for which the information may be used, both at the time of the intended disclosure and at any future time; and
-
be specific as to the date when the authorization expires.
Requirements of signed and written consent, which arose at a time when all records were kept on paper, are still valid, but they will require modification to permit consent by computer, such as by keypad attached to a terminal in a treating physician's office.
The Uniform Act expressly states that the signing of an authorization is not a waiver of any privacy rights that the patient may have under other statutes, rules of evidence, or common law. It further requires that providers (or, in this case, HDOs) retain a copy of each authorization and provides that an authorization may not permit the release of health record information relating to health care that is to be provided more than 90 days in the future. (Exceptions are made for disclosures to third-party payers, but they would be irrelevant for HDOs.) Finally, the Uniform Act states that a patient may revoke a disclosure authorization in writing at any time. Even if consent and participation rights are in place, privacy protection is not ensured, because strategies used to obtain consent, in particular, are fallible. As discussed earlier in this chapter, for example, patients experience substantial pressure to sign authorizations and waivers in order to facilitate both access to and payment for health care.
Release of Person-identified Data
In the seven cases listed in Recommendation 4.3, the committee believes that values other than confidentiality justify access to person-identifiable information with or without consent, and that there exist adequate safeguards for the protection of data in these very limited circumstances. Those values include autonomy for patients in accessing their records, fiduciary responsibility for those unable to care for themselves or make health decisions for themselves, beneficence in providing health care in acute situations, and the social benefits of epidemiologic and health services research. The rationale for each case is described below.
The Standing of Other HDOs
HDOs will need to acquire information about out-of-area care provided to persons in their databases and should be able to do so for those specific circumstances. For example, one HDO might ask another to provide information for state residents of given zip codes who have been hospitalized in other states. The committee concludes that if the requesting HDO has confidentiality and security protections that are at least as stringent as those of the HDO that would be releasing the information, the data should be released. Such HDOs might be in adjoining states (e.g., when Vermont residents are hospitalized in New Hampshire) or within a single state; in other cases they might include overlapping geographical areas such as one or more states and a metropolitan area. In all such cases, individuals might be expected to be found in several different HDOs, and in their best interest (insofar as needed health care is concerned), their data ought to be shared or transferred.
The Standing of Persons, Parents, and Legal Representatives
The second case cited in Recommendation 4.3 is self-evident-when—information about themselves is sought by individuals. The third and fourth cases reflect the need to care for minors and persons who are legally incompetent to give consent for themselves.
One important case concerns the parents of a minor child except when certain actions are protected by state law. Such exceptions include, for instance, family planning services. Emancipated minors are those who live away from home or are in the armed forces and manage their own financial affairs. Mature minors, although still dependent on their parents, are judged to be mature enough to understand the treatment or issue in question and to give informed consent for their own care. The committee believes that privacy and confidentiality for emancipated and mature minors should have the same protection as that given to adults. Parental involvement should be related to the age and development of the minor. Current state laws regarding emancipated or mature minors do not consistently protect such information, and uniform federal legislation is desirable.
The other important case involves legal representatives of incompetent patients. Such legal or personal representatives include guardians as well as individuals who are named in advance directives and granted durable power of attorney.
The Special Standing of Research
The fifth case in Recommendation 4.3—researchers with approval from relevant human subjects committees or institutional review boards (IRBs)—is a different category. In this case person-identified information is not being sought by the patient or for care of the patient, but to conduct studies that in some fashion are regarded to be in the public's interest. Such uses of the databases are considered by this committee to be central and vital to the effective implementation of HDOs. For this reason, researchers whose research design and study plans are deemed appropriate and approved by a review panel—typically but not necessarily an IRB at the lead researcher's university or institution-should be permitted access to person—identified or person-identifiable data in the HDO files.
An IRB is a specially constituted review body established to protect human subjects, usually those recruited for biomedical and behavioral research, when that research is conducted under the auspices of the institution (USDHHS, 1993b). Review and approval by an IRB is required for research that is conducted by investigators supported by a department or agency subject to federal policy. IRBs function under policies set by federal legislation (45 CFR 46 for Department of Health and Human Services; Federal Register, 1991a) and by policies of the institution. Members of the IRB carefully weigh the likely risks and benefits of the proposed research and the procedures and protections for the research subjects.
When research involves only the review of records, such as those in HDOs, the IRB is encouraged to determine that an institutional approval or an expedited review is sufficient. It may do so if it is persuaded: (1) of the significance of the research and that use of data in personally identifiable form is necessary, (2) that any risk of harm to subjects is minimal, (3) that adequate safeguards will be implemented to protect the record or information from unauthorized disclosure, and (4) that removal and destruction of identifiers will be carried out when the research is complete. The committee urges institutions to review applications when requested by serious investigators who many not be affiliated with an institution. Alternatively, such requests might be considered as exceptions by the Data Protection Board on a case-by-case basis.
The committee believes it will usually not be necessary for researchers to obtain consent from record subjects for access to person-identified or -identifiable material, but methods should be incorporated for protecting a record subject's privacy, including notification by the HDO of the uses that may be made of the records.
Contacting potential subjects to obtain further information is a more sensitive matter. It requires careful attention and sensitivity to who would make initial contact and what information would be conveyed to potential subjects or their relatives in the course of the contact. The information conveyed should include the purpose of the study and the kind of data that would be collected, the identity of the persons who will have access to the data, the safeguards that will be used to protect the data from inappropriate disclosure, and the risks that could result from disclosure. Such negotiations should also give written assurance that any publications that result will present the data only in aggregate form so that individuals are not identifiable. Research subjects should also be told if they will be contacted in the future (USDHHS, 1993b).
Special Patient Care Considerations
The sixth case in Recommendation 4.3 involves treating licensed practitioners with a need to know in life-threatening situations, whom the committee believes ought to be able to access data about a patient. This requires that the patient be unable to consent at the time care is rendered. A patient in a situation that threatens loss of life or limb sometimes cannot provide coherent but needed medical information because of mental impairment, stress, or substance abuse and is not considered to be a ''reliable historian." In such cases the committee believes it appropriate to access such data, if available, through the HDO. When the patient cannot be identified, access to the HDO might be particularly helpful if biometric (nonvolitional) identifiers are part of the database.
The committee has chosen the term "licensed practitioner" advisedly, a broader concept than "physician." Circumstances justifying access might occur in a hospital emergency department, in an intensive care unit, or outside the hospital when a health care professional is present and determines that in his or her judgment obtaining certain health information is crucial. All such cases presume that a primary medical record is not available and that no one (patient, family, or friend) can reliably provide needed health information in a timely way.
The seventh case—the release of data to licensed practitioners when treating patients in all other (non-life-threatening) situations, but only with the informed consent of the patient—is the only case in which the committee has recommended the use of informed consent to release of person-identifiable information. Such a circumstance might occur when a treating physician wishes to access the HOD database in addition to the medical records he or she keeps. For example, information on medications prescribed by other practitioners might be pertinent. In such cases, the treating practitioner should obtain explicit consent of the patient. As discussed earlier, consent might be given electronically and might be time limited.
Prohibition on Access to Person-identifiable Data
The committee recommended that HDOs not authorize access to or release of health information on individuals, with or without the informed consent of the individual, in any situation or to any requestor other than those stated above.
To ensure that individuals (i.e., patients, parents of minor children, or legal representatives) are not placed in an untenable situation concerning release of information, the committee has opted for a position that does not rely on consent procedures in most uses or disclosures of data. It prefers to rely on stringent policies against disclosure or release of personal information on individuals. It should be noted that the consent procedures described in this recommendation are for release of information by the HDO. Patients will always be able to consent to release of information by each of their care providers. Nevertheless, in some circumstances the committee envisions that consent procedures will be invoked before HDOs will release person-identifiable information.
The importance of consent as a concept, and adequate procedures for implementing consent, is accentuated by the multiplicity of uses of HDOs. Given this multiplicity, it is difficult to argue that, by providing information, record subjects have implied their consent to subsequent uses and redisclosures. It may well turn out that record subjects will have little or no idea of the number or variety of disclosures that could be made from an HDO.
Implications of Recommendations Denying Access
The reason for prohibiting broad disclosure following patient consent is that HDOs may contain a longitudinal record about all health care delivered to a patient and many personal details about the patient. Permitting the same ritual of consent to authorize disclosure of this information will result in an increased abridgment of patient privacy.
The prohibition on access to person-identifiable information is very broad. If this limitation is enacted into law or such a policy is promulgated by the HDO, it would have several consequences. For example, employers could not obtain information about "out-of-health-plan" use by their employees even for case management purposes. No access for law enforcement would be permissible through compulsory process (if prohibited by federal preemptive legislation). Attorneys could not access the database to build a case on behalf of clients except through compulsory process in accordance with governing law. Secret service agents seeking information about a person suspected of being a security threat to an elected official could not seek information from the HDO.
Prohibiting access could result in some disadvantage or inconvenience to the recordholder as well as possible harm to society. Nevertheless, the committee believes that risks to individual privacy and the importance of a clear and unambiguous policy for HDOs outweigh such possible disadvantages.
In some circumstances, the committee foresees difficult situations that seem to present a conflict between policies. For example, an individual might wish to obtain a copy of his information in the database that he could then supply to an attorney who needs it for a malpractice case or to an employer who demands it for determining new assignments or for case management purposes. The committee, as noted elsewhere, sees little way to "protect" patient information when the individual requests the information from an HDO and then transfers it as he or she sees fit.
Employer Access
RECOMMENDATION 4.4. RESTRICTING EMPLOYER ACCESS
The committee recommends that employers not be permitted to require receipt of an individual's data from a health database organization as a condition of employment or for the receipt of benefits.
Special circumstances exist in the health sector of particular concern to the committee. One involves the current practice of extensive exchange of medical information between employer and payer, with little control by providers or patients. This practice has dramatic implications for patients whose information is accessed by an HDO if the employer and payer are readily able to tap into data in the network. HDOs could make such exchanges of information more harmful to patients because the information exchanged could cover all encounters the patient has with the health care system (not just those covered by insurance or by the employer's health plan).
The committee acknowledges the danger and inappropriateness of these practices. It thus concurs with a recent IOM report (IOM, 1993e) that urged that access to information collected in connection with employment-based health benefits be limited through provisions analogous to those contained in the Americans with Disabilities Act of 1990 (P.L. 101-336).
In Recommendation 4.4, the committee attempts to prohibit the use of HDOs by employers for employment-related decisions about employees. In particular, it seeks to constrain access to person-identifiable data and prevent employers from coercing employees to provide such data about themselves or their families as a condition of employment (e.g., promotion, placement, retention, or termination). This recommendation applies only to the HDO and would not, of course, prevent employers or others from acquiring health information from other sources—examination, a treating physician, an insurer, and so forth.
Employees might wish, however, to provide access to their records to their employer's case managers in circumstances relating to needed health care. To account for this, the committee advises that there be a clear and enforceable division of functions between employment and personnel decisions of an employer and the employer's health benefits administration and case management. In the absence of state or federal legislation limiting access and threatening liability, employers should at least promulgate and enforce such internal policies.
Universal Person Identifiers
Unique, individual person identifiers are essential to facilitate the efficient operation and data interchange of HDOs. The committee also recognizes the strong arguments against the use of the SSN as that unique identifier. The great majority of the committee agreed on the need for a new unique identifier of the grounds that the SSN offers too many opportunities to breach confidentiality. The creation of a new number would: (1) permit legislative protection of that number, (2) offer the possibility of greater protection for health information than is possible with the SSN, and (3) could occur at the time of implementation of universal health care coverage, which will, if enacted, require some scheme for unique identification.
COMMENT
In this report the committee has addressed its views and concerns about a new entity in health care delivery and recordkeeping—the HDO. Little is really understood about how HDOs will function, what effects they will really have as opposed to the benefits they are expected to offer, and how they will evolve over the next decade or so. These matters will be worked out in an environment of change and stress, as the nation sorts out its posture toward health care and health reform. This report, therefore, must be seen as laying the groundwork for the context in which HDOs come into being and function. It cannot be read as providing answers to all HDO issues that may arise, but neither could the committee ignore the future completely.
In matters of privacy, the unique aspects of the HDO are two: (1) the concentration of medical information about very large numbers of individuals, coupled with (2) the large number of end users who have authorized access to some or all of an individual's record. The HDO will inevitably lead to much more varied use of health care information, and therein is a privacy issue of substantial significance for the future.
Undoubtedly, both anticipated and innovative uses of HDO databases will be evolutionary. In an operational sense, this is probably wise and unavoidable; in matters of privacy, it is risky because a small number of seemingly innocuous uses can cumulatively create a substantial privacy risk. Some uses that arise will prove repugnant to society and will be impermissible; others will be considered annoying, but will be tolerated. Some could be so discriminatory or otherwise distasteful that they might well be proscribed by law.
The committee notes that the privacy dimension of medical records, regional databases, and HDOs is not a matter that can be examined once and thereafter ignored. New dimensions of privacy will arise, as will extensions of old concerns, new threats to privacy, and new uses of data that prove unwise. From time to time, perhaps every few years in the beginning of the "HDO movement," the privacy issue needs to be revisited and reevaluated. New mechanisms for assuring privacy may need to be invented; new actions by Congress may be needed.
Security safeguards that protect the confidentiality of data and the automated systems themselves have similar characteristics. New threats will materialize; penetrators will become more skilled; new motivations for surreptitiously acquiring health data will appear. From time to time, the safeguards will need upgrading and strengthening.
The New Privacy
Privacy concerns have centered historically on the use of information about an individual that governs some decision about her (e.g., a right, entitlement, or privilege) or some action taken for or against her. The benefit or harm as well as the risk of information misuse applies to the same individual.
With the growth of an information industry that deals widely with information about people, the benefit-risk aspect has changed; the benefit has turned toward organizations and society, but the risk has remained for the individual. The traditional recordkeeping characterization of privacy is far too limited given the intense pace of automation in recordkeeping and the electronic linkages of systems of all kinds.
Conflicts have already begun to appear with regard to medical data. The most frequently quoted anecdote is that of the pharmaceutical company that uses patient drug use as the basis for targeted mailings and advertising. Some people will tolerate such nonmedical use of health data as an annoyance; others will feel strongly about it; some will be harmed because a mailing can reveal a medical condition that was being concealed. Employer use of health data also brings two motivations into conflict: that of the employer who, having paid for the health care in whole or in part, feels it is entitled to have the data for more efficient management of the organization and that of the individual who considers that health data are personal and to be shared only as he sees fit.
Other conflicts will arise, and the concentration of so many kinds of information in an HDO will be a stimulus to their further creation. Looking well to the future, therefore, a Code of Fair Health Information Practices is likely to be necessary. It need not be exactly like the one in the federal Privacy Act; indeed, it would probably have additional provisions for controlling the use of health data.
For example, society has not yet expressed its view on how very sensitive kinds of medical information can be used; genetic data is a case in point. It may be decided that prohibitions against particular uses of information will be accepted. If so, then one mechanism for implementation is incorporation of the prohibition, possibly stated in a very general way, into a fair code; another is to cast it into law. There is precedent for such prohibitions; for example, personnel forms cannot ask certain kinds of questions such as those dealing with religion or sexual orientation.
For the most part, privacy law in this country has been formulated under the assumption that holders of information about people may generally do with it what they please, constrained only by corporate ethics and the good taste of business, societal acceptance (or outrage), occasional attention by the government, pressures of consumer activist groups, and the consequences of legal actions brought by individuals or consumer groups. This historical view may prove inappropriate or even dangerous in regard to health data. There is now evidence that the American public agrees. Westin has found high medical privacy concerns among 48 percent of respondents and high privacy concerns in general among 25 percent of survey respondents whom he terms Privacy Fundamentalists. This group would seek sharp limits on organized data collection and legal protection for privacy. Another 57 percent of the public has been termed Privacy Pragmatists. He describes this group as examining each situation to see whether information is really needed for a legitimate societal function and whether safeguards are being followed. The final group he calls Privacy Unconcerned. This small group is not apprehensive about the use of personal data (Harris/Equifax, 1993).
Our society and country are designed to operate with what the engineer would call feedback, or what society would call controls, weakly defined and often ad hoc or de facto. The country, its people, its government, and its institutions have survived thus far under this paradigm. With the coming concentration of health information about huge numbers of people in the HDO, is this an acceptable national posture for information that is potentially the most sensitive of all data ever collected about people?
It is difficult to attempt answers to a question such as this because the near future of health care is so poorly defined. Events under way—for example, national health care reform—will have a major impact on the motivations of managers in charge of health care providers.
The country might be safe with the perception and handling of privacy as it has been done for over two decades, but it might not. There can easily arise distasteful practices in the way health care information is exploited for other than delivery and payment of care. It is simply not known which uses of health care information will be acceptable to society, will wisely serve the needs of society and the health care industry, and will strike an acceptable balance between the desires of a profit-oriented health care industry (which may be ever more prevalent in the future) and the invasion-of-privacy consequences for patients. In short, the privacy dimension of health care information is dynamic, and it must be treated accordingly.
SUMMARY
The committee has examined sources of concerns about informational privacy and the confidentiality of health-related information and security, and it defines each in the context of health information. After a review of privacy rights, confidentiality obligations and disclosure policies, and disclosure as it is treated by law and in practice, the committee concluded that there was much basis for concern about confidentiality, but little applicable legal guidance for HDOs. It reviewed options related to uniform legislation, consent and participation rights, disclosure policies, and governance, and advanced a set of recommendations favoring strong federal preemptive legislation and responsible organizational policies to protect privacy and confidentiality of person-specific information.
In the context in which "confidential" is a designation given data to be protected in terms of security and access, the committee has made a number of recommendations that would help HDOs achieve these ends. First, confidentiality is addressed by a recommendation for preemptive federal legislation that all health care data be confidential, protected as such, and access to it controlled.
Second, the committee recommends the establishment of data protection and data integrity boards to provide oversight of security and access in HDOs. To implement protection of health care data, the committee has addressed security and recommended that automated systems and networks supporting HDOs have comprehensive system and network security that reflect the state of the art.
Third, to address patient privacy rights, the report has recommended that patients can have access and other rights regarding their records, and be dealt with through a code of fair health information practices. To accommodate patient expectations of privacy, the committee recommended that patients have certain legally assured rights to recover damages and force compliance if health care information is misused, abused, or improperly released to unauthorized parties.
Fourth, to address privacy—the issue of access to personal information—the committee has made recommendations concerning who should and should not have access to person-identified information and under what circumstances.
- 1
-
In October 1993, Equifax, a credit reporting company, released the results of a Louis Harris poll, the most recent in a series of surveys commissioned by Equifax and conducted periodically since 1978. For the first time, the 1993 survey assessed the beliefs and attitudes about privacy and disclosure of health information of a sample of the public and of "health leaders." A number of the survey questions bear directly on the issues addressed in this chapter.
- 2
-
The OTA report was released just as the IOM report was being completed.
- 3
-
The Administration's Health Security Act (HSA, 1993) calls for the development of Health Information System Standards within two years of its enactment to promulgate standards and security safeguards for the privacy of individually identifiable health information that is in the health information system (see Footnote 1, Chapter 2). The proposed legislation states the following principles: (1) All disclosures of individually identifiable health information by an individual or entity shall be unauthorized unless (a) the disclosure is by the enrollee identified in the information or whose identity can be associated with the information; (b) the disclosure is authorized by such enrollee in writing in a manner prescribed by the Board; (c) the disclosure is to Federal, State, or local law enforcement agencies for the purpose of enforcing this Act or an Act amended by this Act; or (d) the disclosure otherwise is consistent with this Act and specific criteria governing disclosure established by the Board. Further, disclosure of individually identifiable health information shall be restricted to the minimum amount of information necessary to accomplish the purpose for which the information is being disclosed. It would require that any individual or entity who maintains, uses, or disseminates individually identifiable health information implement administrative, technical, and physical safeguards.
It stipulates that an enrollee (or an enrollee representative) has the right to know (a) "whether any individual or entity uses or maintains individually identifiable health information concerning the enrollee; and (b) for what purposes the information may be used or maintained" (Sec. 5120). It also specifies a right to access to see, copy, and have entered a notation of any amendment or correction of his or her information. It specifies a right to receive a written statement concerning (1) the purposes for which individually identifiable health information may be used or disclosed by, or disclosed to, any individual or entity; and (2) the right of access described above. The legislation also calls for the use of a unique identifier to be used in transmitting information. It further specifies that individually identifiable health care information may not be used in making employment decisions.
Sec. 5121 calls for the National Health Board to sponsor (1) research relating to the privacy and security of individually identifiable health information; (2) the development of consent
- 4
-
An IOM report on assessing genetic risk explores these issues in considerable detail and develops a strong pro-privacy stance (IOM, 1993b).
- 5
-
In the United States, privacy is restricted to real persons. In Europe, legal persons are generally included.
- 6
-
See, Plante v. Gonzalez, 575 F. 2d 1119, 1123 (5th Cir. 1978). However, in J.P. v. DeSanti, 653 F. 2d 1080, 1090 (6th Cir. 1981), the Sixth Circuit held that the Constitution's right-to-privacy standard does not extend to the disclosure of personal information.
- 7
-
In a California case, Tarasoff v. Regents of the University of California, 17 Ca. 3d 425,551 P.2d (1976), a psychiatrist who was told of a patient's homicidal fantasies regarding the patient's girlfriend did not warn her because he believed that confidentiality constraints prevented him from doing so. Soon after, the patient killed the woman. The court found that the physician had a duty to warn third parties in such circumstances.
- 8
-
A suit brought by an AIDS patient under the name John Doe against Shady Grove Adventist Hospital resulted in the hospital's trying to force the patient to reveal his true name to the press and public (John Doe v. Shady Grove Adventist Hospital, et al., 89 Md. App. 351, 598 A.2d 507 [1991a]).
- 9
-
Waller (1991) provides a detailed discussion of legal considerations affecting computer-based patient records, including privacy rights.
- 10
-
The report of the Secretary's Advisory Committee on Automated Personal Data Systems, Records, Computers and the Rights of Citizens (USDHEW, 1973) was a ground-breaking report of the Secretary of Health, Education, and Welfare that articulated five fair information practice principles, including the secondary use principle. The Federal Privacy Act at 5 U.S.C. § 552a(b) reflects the secondary use principle by permitting nonconsensual secondary uses of personal data only for purposes that are consistent with the purpose for which the data were first collected.
- 11
-
A recent case upheld the right of any employer to change (and thereby reduce) its health insurance benefits to reduce exposure. In McGann v. H&H Music Co, 742 F. Supp. 392, affd 946 F.2d 401, after a current employee was diagnosed with AIDS, his employer changed the health benefit plan to become self-insured and subsequently established a $5,000 limitation on AIDS-related medical expenses.
- 12
-
For a history of the national identification debate in this country, see Department of Justice, 1976; Burnham, 1983; U.S. Senate, Subcommittee on Courts, Committee on the Judiciary, 1983; and Shattuck, 1984; Eaton, 1986.
- 13
-
The term check digits is often used as short hand for error correcting and detecting codes used extensively in modern computers and communications systems. It is sometimes suggested, almost casually as though it were a magic solution, that the addition of a check digit to the Social Security number would allow the verification of its accuracy. The addition of extra characters could in principle accomplish a number of tasks, including:
- 14
-
The most comprehensive treatment of the SSN as a recordkeeping personal identifier in the government is in the PPSC report (1977a) and the report of the Secretary's Advisory Committee (USDHEW, 1973). An examination of the latter also examines the role of the SSN in some commercial and private-sector circumstances. Hibbert (1992) gives a brief overview of the SSN in recordkeeping with advice for the individual in controlling its use.
- 15
-
For example, some large-volume retail stores in the Washington, D.C., area routinely ask for a customer's Social Security number when he or she pays for any purchase by check.
- 16
-
Note, however, that FOIA would not necessarily exempt physicianor provider-specific information as discussed in Chapter 3.
- 17
-
The federal Privacy Act contains 12 exceptions that permit disclosures without obtaining subject consent. One such exemption is for research purposes (Federal Register, 1991b). Personally identifiable health record information held by Medicare peer review organizations can be shared with authorized researchers without subject consent.
- 18
-
Other federal laws address the use of personal information in an immense array of circumstances and settings: criminal justice information systems; student records and tests; tax information; financial information held by banks and other financial institutions including electronic transfers of funds; press offices; and identification of intelligence officers, bad debtors, cable service users, renters of videotapes, and rape victims. Confidentiality provisions also appear in statutes pertaining to the national census, Social Security, child abuse information, and federally supported drug and alcohol treatment facilities (OTA, 1986). Such protections are often filled with lists of exceptions, however, sometimes to the point of effectively negating the purpose of the legislation.
- 19
-
Some state and federal laws will restrict the ability of providers to disclose medical record information to HDOs, at least in the absence of patient consent or a legislative mandate. In addition, in some states it may be difficult or impossible to word a patient consent to such disclosure that does not result in waiver of the physician-patient privilege.
- 20
-
Notification is included as one of the recommendations of the IOM committee studying privacy and confidentiality protections in the genetics testing environment (IOM, 1993b).
- 21
-
The Health Care Authority of Washington State issued draft recommendations for health information systems in September 1992 (6.7[4]; pp. 78-79). Among the draft recommendations were seven related to access to person-specific information. Access would be permitted only for the following specified purposes: use by the individual affected; use by service providers in the course of providing health services (subject to standards of client consent); use in payment, utilization review, and eligibility or plan membership processes; legally required reporting of births, deaths, communicable diseases, and other information; to carry out or cooperate with epidemiologic investigation of disease outbreaks by state or local public health authorities; for confidential research, when properly authorized by an institutional review board; and to establish linkage among data sources necessary to avoid duplicative data collection burden.
- 22
-
Even if HDOs chose never to release person-identified or -identifiable data, and notwithstanding that the record subject had authorized release, HDOs would still be obliged to provide the person directly with a copy of his or her record. Nothing would stop that individual from personally delivering a copy of the record to a third-party requestor.
- 23
-
When capitalized, the phrase "Fair Information Practices" refers to procedures established in the Privacy Act of 1974. When used without capital letters it is a generic phrase with a broader or narrower meaning, depending on the context.
- 24
-
Good information practices include good security practices. A strong stance on privacy requires strong and comprehensive system and network security. Whether federal legislation would establish security practices and procedures or whether such policies would be left for promulgation by the HDOs, however, was considered by the committee to be beyond the scope of its charge.
- 25
-
This term is used by some privacy advocates, and particularly in Europe, to mean a top-level federal entity. It is also described in the proposal for the Health Security Act (1993). It is used here in a more general sense and intended to refer to units that any type of HDO, of any size, might create and support.
- 26
-
If the HDO is not a governmental agency and is not authorized by law to do so, it cannot impose penalties.
- 27
-
This committee has proceeded on the assumption that HDOs will not be the repository of the primary medical record. If they were, then they would need to retain records for longer periods of time in order to defend against malpractice suits and, in some cases, to comply with state record retention requirements.
- 28
-
Specific concerns include physical risk management for disasters (e.g., fire, flood); memory protection and backup in case of hardware failure; design and use of audit trails, log-on procedures, antivirus protection for software; assignment and monitoring of badges and other mechanisms to control personnel access; logging and cataloging of magnetic tapes and floppy disks; destruction of paper containing sensitive printouts and other documents; and monitoring the system for unauthorized access.
Incomplete Coverage Of A Topic Violates Which Of These Four Writing Criteria?
Source: https://www.ncbi.nlm.nih.gov/books/NBK236546/
Posted by: mccluskeyvarty2001.blogspot.com

0 Response to "Incomplete Coverage Of A Topic Violates Which Of These Four Writing Criteria?"
Post a Comment